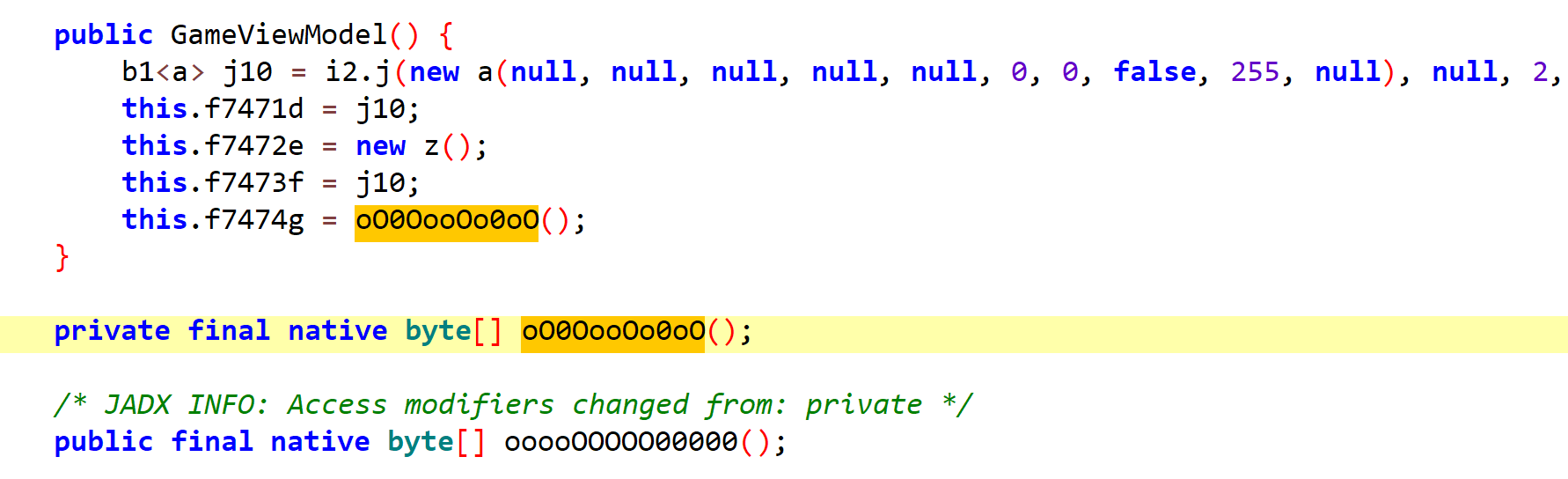
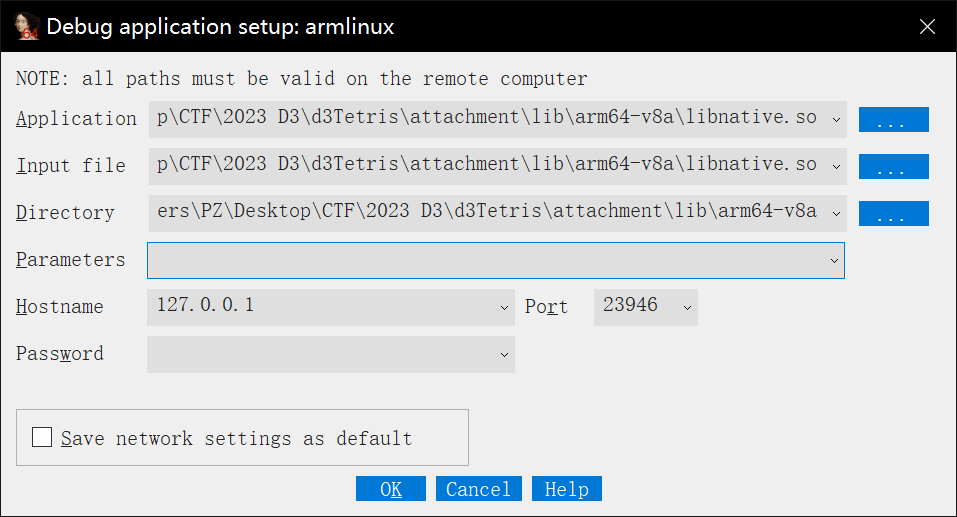
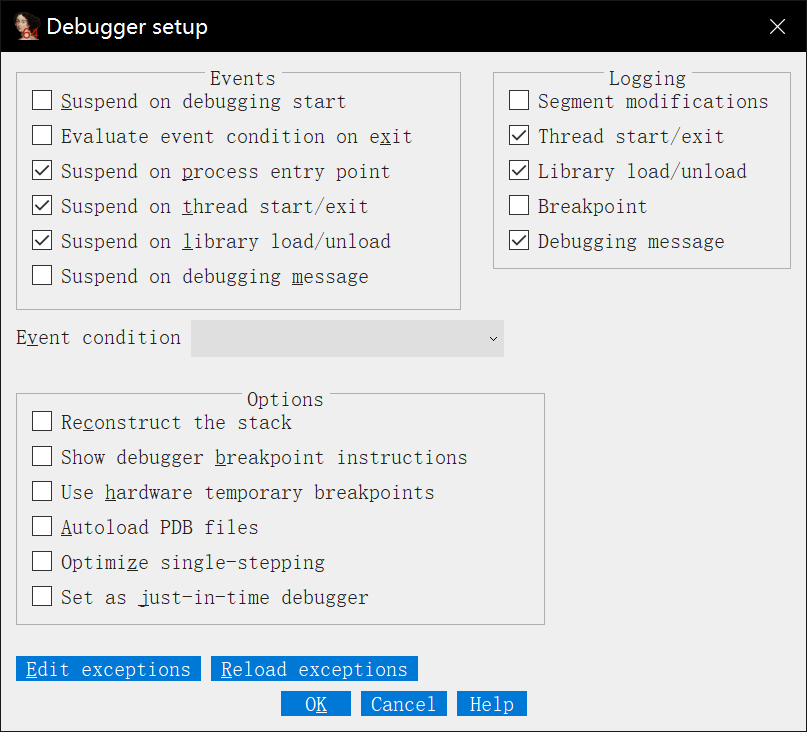
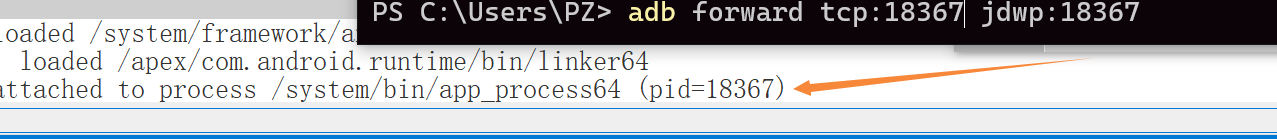
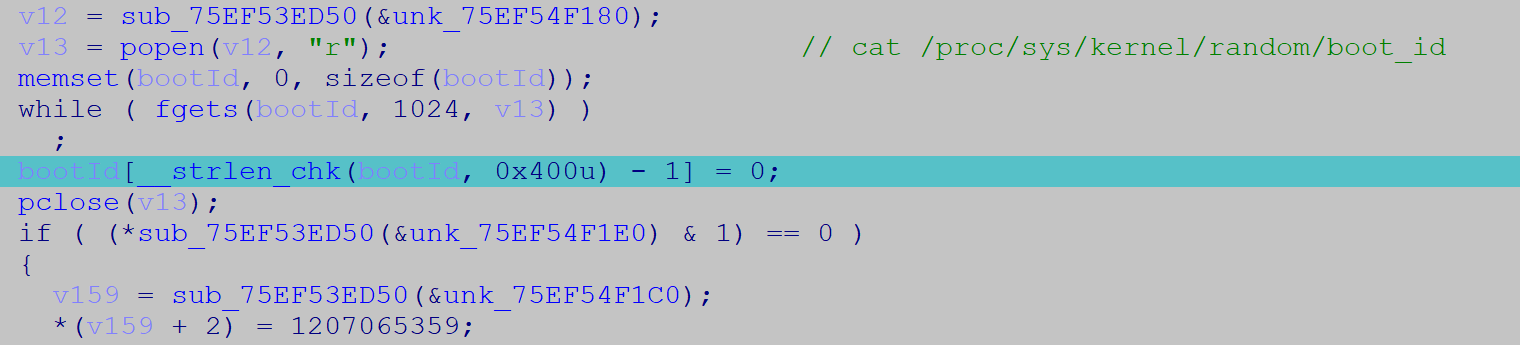
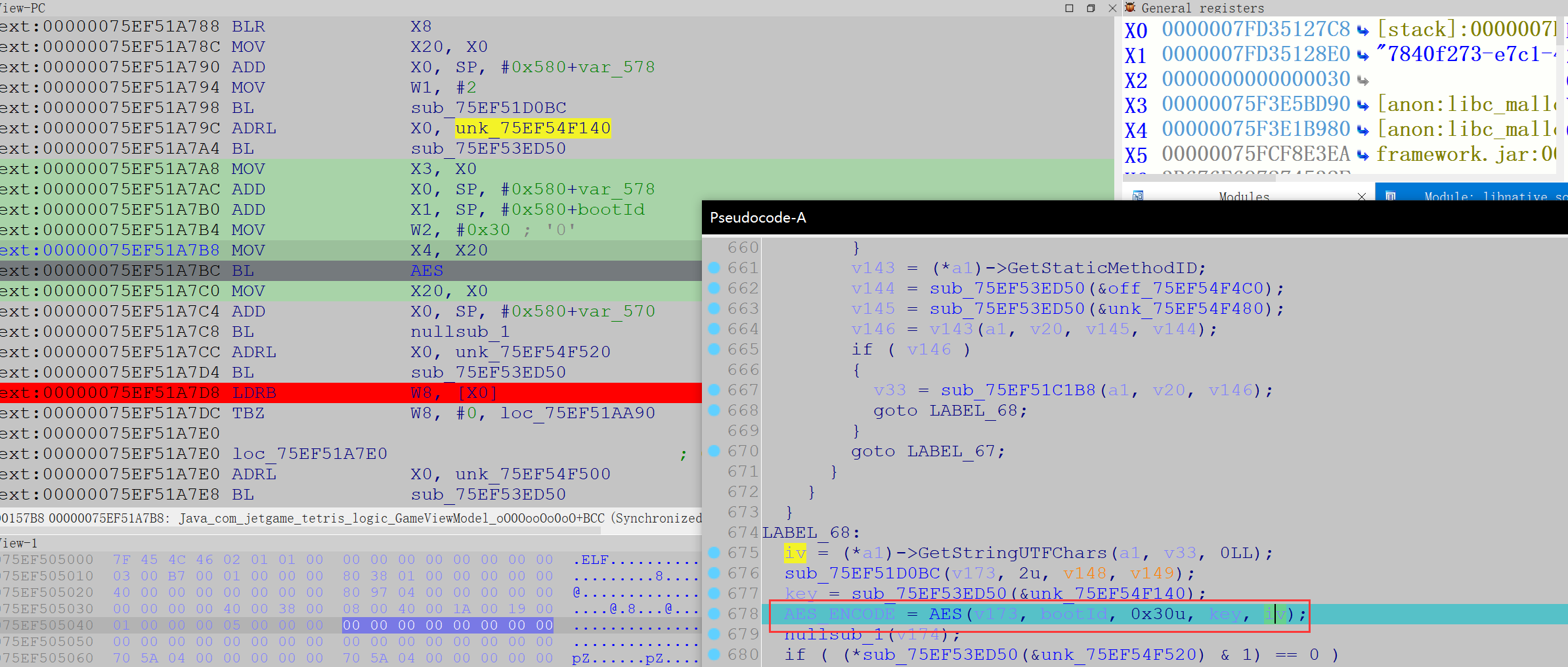
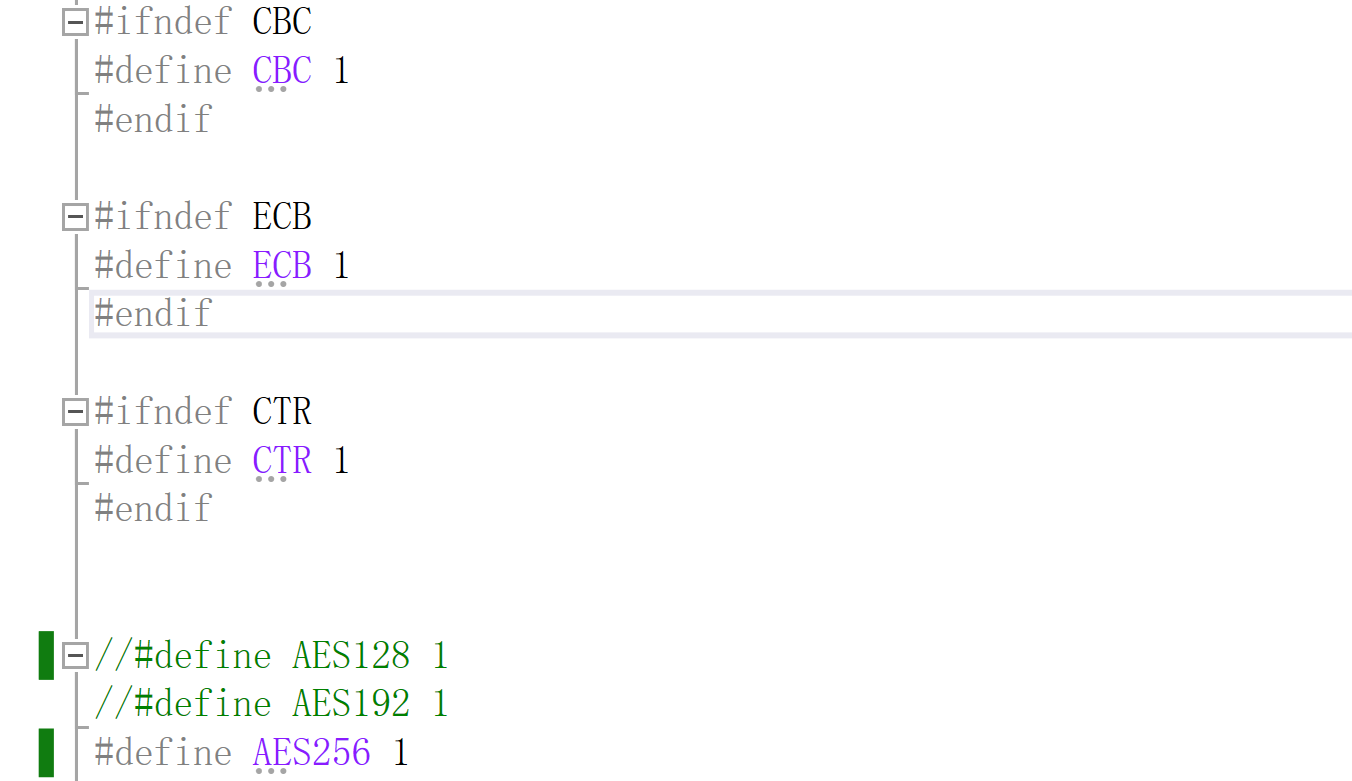
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
324
325
326
327
328
329
330
331
332
333
334
335
336
337
338
339
340
341
342
343
344
345
346
347
348
349
350
351
352
353
354
355
356
357
358
359
360
361
362
363
364
365
366
367
368
369
370
371
372
373
374
375
376
377
378
379
380
381
382
383
384
385
386
387
388
389
390
391
392
393
394
395
396
397
398
399
400
401
402
403
404
405
406
407
408
409
410
411
412
413
414
415
416
417
418
419
420
421
422
423
424
425
426
427
428
429
430
431
432
433
434
435
436
437
438
439
440
441
442
443
444
445
446
447
448
449
450
451
452
453
454
455
456
457
458
459
460
461
462
463
464
465
466
467
468
469
470
471
472
473
474
475
476
477
478
479
480
481
482
483
484
485
486
487
| #include <cstdio>
#include <cstring>
#include "defs.h"
#include <cstdlib>
#define _CRT_SECURE_NO_WARNINGS
unsigned short op[2772] = {
0x0015, 0x0000, 0x0000, 0x0000, 0x0000, 0x0000, 0x0000, 0x0000,
0x0000, 0x0000, 0x0000, 0x0000, 0x0000, 0x0000, 0x0000, 0x0000,
0x0000, 0x0000, 0x0000, 0x0000, 0x0001, 0x0A16, 0x0A9C, 0x000A,
0x0061, 0x00DA, 0x006E, 0x008E, 0x0012, 0x0065, 0x00EA, 0x0086,
0x000D, 0x0A96, 0x0A45, 0x008D, 0x0043, 0x0023, 0x00F5, 0x00A4,
0x0080, 0x006D, 0x0064, 0x009F, 0x00CF, 0x0AF8, 0x0A4B, 0x00F0,
0x0072, 0x00BD, 0x000F, 0x004E, 0x00ED, 0x0092, 0x006F, 0x00AE,
0x0060, 0x0A4E, 0x0A3E, 0x00D1, 0x009D, 0x0005, 0x0018, 0x00E7,
0x0013, 0x0031, 0x0009, 0x008C, 0x0017, 0x0A14, 0x0A29, 0x00A0,
0x00E8, 0x001A, 0x0015, 0x001B, 0x003A, 0x00ED, 0x001F, 0x00C7,
0x0003, 0x0A2C, 0x0AC6, 0x0078, 0x0091, 0x004E, 0x0009, 0x0062,
0x00C7, 0x0020, 0x005E, 0x0064, 0x00F2, 0x0003, 0x0052, 0x0049,
0x0065, 0x00FF, 0x00F1, 0x00E4, 0x002F, 0x0064, 0x0027, 0x00E6,
0x0AFB, 0x00D4, 0x00B6, 0x000D, 0x0051, 0x003E, 0x0042, 0x0029,
0x004D, 0x00A3, 0x00DD, 0x0067, 0x0AEC, 0x00DD, 0x0020, 0x00F2,
0x000D, 0x005F, 0x0011, 0x005D, 0x0097, 0x009E, 0x002C, 0x0020,
0x0AED, 0x009E, 0x0044, 0x00B2, 0x0002, 0x00EA, 0x0020, 0x0039,
0x00F8, 0x0000, 0x0011, 0x0079, 0x0ACA, 0x00AE, 0x0075, 0x00AB,
0x0032, 0x0003, 0x00D2, 0x00FC, 0x0088, 0x0044, 0x005F, 0x00FC,
0x0ADF, 0x0064, 0x001E, 0x0004, 0x007E, 0x0024, 0x0045, 0x00EF,
0x002A, 0x0036, 0x00D1, 0x0025, 0x0AE6, 0x00EB, 0x0047, 0x00EC,
0x0081, 0x0069, 0x00E1, 0x0046, 0x0085, 0x0011, 0x00E3, 0x002B,
0x0A9E, 0x0099, 0x00D0, 0x0095, 0x0032, 0x00ED, 0x0097, 0x00CB,
0x006E, 0x00B4, 0x003C, 0x0009, 0x0A1F, 0x00A1, 0x009C, 0x0083,
0x006D, 0x0070, 0x0009, 0x0078, 0x00FE, 0x00A2, 0x0090, 0x00D5,
0x0A3F, 0x00F9, 0x00E5, 0x0015, 0x00B9, 0x0063, 0x0023, 0x00B6,
0x0024, 0x00B4, 0x00DD, 0x00F1, 0x0A56, 0x007C, 0x0070, 0x000F,
0x0007, 0x005A, 0x005E, 0x0099, 0x0012, 0x0028, 0x00C2, 0x0095,
0x0AAA, 0x00AF, 0x00B7, 0x00A3, 0x0032, 0x0029, 0x0086, 0x00D9,
0x008C, 0x008F, 0x00FA, 0x009D, 0x0A5C, 0x0028, 0x00B4, 0x001C,
0x00C1, 0x0013, 0x002C, 0x0023, 0x0072, 0x0083, 0x00A4, 0x007E,
0x0A1E, 0x003A, 0x0048, 0x004A, 0x007C, 0x00B1, 0x0011, 0x0009,
0x00CE, 0x00FB, 0x0045, 0x00BA, 0x0AC8, 0x00F7, 0x001E, 0x00AC,
0x0055, 0x0048, 0x0082, 0x00B5, 0x005D, 0x00A7, 0x005F, 0x0092,
0x0A64, 0x004F, 0x009B, 0x0022, 0x0054, 0x000E, 0x00FC, 0x0009,
0x0008, 0x000A, 0x0043, 0x00D8, 0x0A60, 0x00B4, 0x00BB, 0x006D,
0x0036, 0x0037, 0x002E, 0x0054, 0x009D, 0x006B, 0x0079, 0x00E2,
0x0AE4, 0x00A5, 0x0047, 0x0094, 0x0062, 0x00E8, 0x002E, 0x00E0,
0x00AD, 0x009E, 0x00B2, 0x0020, 0x0A44, 0x0064, 0x0041, 0x0011,
0x00A1, 0x0060, 0x009E, 0x002F, 0x005B, 0x006F, 0x0000, 0x0039,
0x0A87, 0x0077, 0x00F6, 0x00E6, 0x0086, 0x006D, 0x003F, 0x00A1,
0x003F, 0x00C5, 0x002F, 0x0092, 0x0ABF, 0x004B, 0x0025, 0x000B,
0x0035, 0x006E, 0x006B, 0x00A7, 0x0058, 0x00E6, 0x0055, 0x00EC,
0x0AAA, 0x000C, 0x00D6, 0x009E, 0x0053, 0x0035, 0x00BA, 0x007B,
0x0036, 0x0095, 0x00CD, 0x00DC, 0x0A52, 0x0056, 0x00EC, 0x0059,
0x00B3, 0x005E, 0x00A7, 0x003D, 0x00C8, 0x0090, 0x00D7, 0x00F9,
0x0A5D, 0x0009, 0x003C, 0x005F, 0x00B1, 0x00A8, 0x00C5, 0x00E3,
0x00D8, 0x0047, 0x0097, 0x00CD, 0x0AB3, 0x0059, 0x0024, 0x00F3,
0x007E, 0x0047, 0x0022, 0x0016, 0x00E4, 0x001D, 0x0052, 0x0012,
0x0A05, 0x0024, 0x00D2, 0x0086, 0x00DA, 0x0096, 0x00E4, 0x004E,
0x001B, 0x0037, 0x0037, 0x0069, 0x0ABB, 0x0021, 0x0004, 0x00FD,
0x0088, 0x0025, 0x004C, 0x001C, 0x00F0, 0x0014, 0x00AE, 0x008B,
0x0A6E, 0x00DE, 0x0097, 0x00FE, 0x00EE, 0x00E3, 0x007D, 0x00C1,
0x00C2, 0x003C, 0x00A4, 0x0064, 0x0A55, 0x0088, 0x004F, 0x00F0,
0x0082, 0x00C8, 0x0098, 0x005E, 0x00FB, 0x0058, 0x003C, 0x0005,
0x0A77, 0x0019, 0x0053, 0x006A, 0x00F9, 0x00A3, 0x0029, 0x0011,
0x00B5, 0x00BA, 0x00A7, 0x00F8, 0x0AC4, 0x00C4, 0x0052, 0x00B3,
0x003E, 0x00C2, 0x00A1, 0x00D7, 0x00E0, 0x0014, 0x0018, 0x00F9,
0x0AAB, 0x0024, 0x00D4, 0x0020, 0x0080, 0x003E, 0x0040, 0x009B,
0x00D3, 0x00AE, 0x008B, 0x00B1, 0x0A37, 0x0053, 0x00F1, 0x0062,
0x0038, 0x005D, 0x0020, 0x0000, 0x00C2, 0x00D8, 0x00E3, 0x00E4,
0x0A73, 0x00D4, 0x00E2, 0x0008, 0x00FD, 0x00E6, 0x00FC, 0x00AD,
0x004F, 0x0087, 0x00A3, 0x00D4, 0x0A47, 0x0024, 0x00A2, 0x0031,
0x008C, 0x0004, 0x0061, 0x0081, 0x001B, 0x003F, 0x008C, 0x0010,
0x0A14, 0x0099, 0x00FF, 0x00A9, 0x00AD, 0x00FC, 0x0008, 0x0034,
0x003D, 0x00B0, 0x007B, 0x0020, 0x0A63, 0x002D, 0x00C8, 0x00D0,
0x0029, 0x004E, 0x002E, 0x0078, 0x00E9, 0x00DF, 0x00DA, 0x00F8,
0x0A4A, 0x0A2B, 0x0A10, 0x00DA, 0x0041, 0x0A95, 0x0012, 0x0A1A,
0x0A98, 0x00A8, 0x0024, 0x0AE7, 0x0066, 0x004D, 0x0007, 0x00E0,
0x0AC1, 0x0A66, 0x00E7, 0x0048, 0x0AB3, 0x00E0, 0x0A7F, 0x0A6D,
0x0088, 0x00E7, 0x0AEA, 0x0065, 0x00C7, 0x00E1, 0x0019, 0x0002,
0x00B9, 0x0075, 0x00DF, 0x0035, 0x0025, 0x0003, 0x003B, 0x00D4,
0x00F6, 0x0028, 0x0091, 0x00E8, 0x00C4, 0x0059, 0x0AE6, 0x0AD2,
0x0064, 0x00A0, 0x002E, 0x0060, 0x00B6, 0x00D4, 0x006C, 0x00EE,
0x0AD3, 0x00AB, 0x00CF, 0x00BB, 0x0021, 0x0AFC, 0x0A0C, 0x0031,
0x0000, 0x0A32, 0x0051, 0x0AC3, 0x0A15, 0x00C6, 0x0023, 0x0AB2,
0x00CE, 0x0032, 0x00A7, 0x001B, 0x0AEC, 0x0A9C, 0x002F, 0x0075,
0x0ACC, 0x008B, 0x0A4F, 0x0ACD, 0x0005, 0x00AF, 0x0AB1, 0x0055,
0x0080, 0x00C0, 0x009D, 0x009C, 0x0034, 0x0090, 0x0092, 0x00EC,
0x0002, 0x0032, 0x0015, 0x00DF, 0x002E, 0x009B, 0x0026, 0x00B9,
0x0070, 0x0001, 0x0AEB, 0x0AD8, 0x006B, 0x0018, 0x0089, 0x0086,
0x00E5, 0x0016, 0x00C2, 0x00E0, 0x0A26, 0x008D, 0x0064, 0x000B,
0x00FC, 0x0A05, 0x0A52, 0x001A, 0x008C, 0x0A26, 0x0017, 0x0A3D,
0x0A17, 0x003C, 0x0011, 0x0AEC, 0x00D4, 0x0014, 0x00A2, 0x005D,
0x0AEB, 0x0A93, 0x00CC, 0x00A6, 0x0A1A, 0x0073, 0x0AD2, 0x0AAF,
0x0077, 0x0012, 0x0A36, 0x0077, 0x0047, 0x00CD, 0x00D5, 0x00AF,
0x0036, 0x00F2, 0x00CE, 0x00B2, 0x0023, 0x003A, 0x00B3, 0x00F3,
0x0045, 0x0003, 0x00F4, 0x00A7, 0x00EE, 0x00CF, 0x0A3C, 0x0AA7,
0x0012, 0x00A9, 0x0061, 0x005F, 0x00A7, 0x0090, 0x0046, 0x00DB,
0x0A41, 0x0034, 0x00C4, 0x0034, 0x0038, 0x0A52, 0x0A13, 0x0016,
0x00AD, 0x0AB7, 0x0021, 0x0A0E, 0x0A24, 0x006C, 0x0018, 0x0AE5,
0x0092, 0x0061, 0x00CF, 0x00AB, 0x0AC0, 0x0AA3, 0x0071, 0x00D9,
0x0A13, 0x00DB, 0x0A3C, 0x0A8B, 0x0012, 0x0019, 0x0A2A, 0x0002,
0x00C3, 0x0096, 0x00ED, 0x006E, 0x0024, 0x00FA, 0x00C4, 0x0085,
0x0075, 0x00FE, 0x0050, 0x0007, 0x00E8, 0x000A, 0x00E6, 0x0041,
0x0082, 0x0012, 0x0A83, 0x0AD9, 0x007C, 0x005E, 0x004E, 0x0015,
0x004F, 0x001B, 0x005E, 0x00C3, 0x0AFC, 0x0030, 0x00FB, 0x0076,
0x0058, 0x0AC3, 0x0A3A, 0x0033, 0x0044, 0x0A1B, 0x009C, 0x0AB9,
0x0A7C, 0x0008, 0x004B, 0x0A17, 0x0070, 0x0082, 0x00BC, 0x00F3,
0x0A01, 0x0AEF, 0x00C5, 0x0062, 0x0A9F, 0x002A, 0x0A09, 0x0ACD,
0x003F, 0x0086, 0x0A8B, 0x00C5, 0x0087, 0x0045, 0x00EA, 0x00DE,
0x0014, 0x00BD, 0x00FE, 0x00F8, 0x00C6, 0x00BB, 0x00D9, 0x009E,
0x006A, 0x0083, 0x0013, 0x0063, 0x006A, 0x00AF, 0x0AD0, 0x0AC0,
0x00C9, 0x00F6, 0x002F, 0x0062, 0x0088, 0x00DF, 0x00E2, 0x0090,
0x0AC4, 0x0069, 0x0095, 0x0050, 0x0082, 0x0A6A, 0x0AB1, 0x00F1,
0x003E, 0x0A22, 0x002A, 0x0A1F, 0x0A66, 0x007B, 0x0089, 0x0AB8,
0x0030, 0x004B, 0x00BB, 0x0031, 0x0AF1, 0x0A8E, 0x00DC, 0x00D4,
0x0AB2, 0x00F3, 0x0AF0, 0x0A1D, 0x008C, 0x00CA, 0x0A57, 0x0087,
0x00C3, 0x009C, 0x00FB, 0x007E, 0x0053, 0x00B6, 0x0033, 0x00BA,
0x00F2, 0x00BB, 0x0009, 0x0054, 0x00A1, 0x0072, 0x0088, 0x00A4,
0x00D3, 0x0070, 0x0ACC, 0x0AFB, 0x004F, 0x002E, 0x008B, 0x0031,
0x0040, 0x000E, 0x00B8, 0x009A, 0x0A44, 0x00AC, 0x00FF, 0x00F1,
0x00F5, 0x0A7B, 0x0A95, 0x0077, 0x0057, 0x0A3D, 0x0092, 0x0A0A,
0x0A6E, 0x0017, 0x00E4, 0x0ABD, 0x0075, 0x005D, 0x008D, 0x0023,
0x0A84, 0x0A76, 0x00A1, 0x00F6, 0x0A03, 0x003D, 0x0AB1, 0x0A87,
0x0055, 0x0037, 0x0A0F, 0x0093, 0x001A, 0x001A, 0x0002, 0x00F1,
0x0018, 0x0005, 0x009A, 0x008A, 0x0013, 0x001A, 0x0087, 0x001B,
0x0045, 0x007E, 0x0023, 0x0077, 0x008B, 0x0094, 0x0AF2, 0x0ABE,
0x00BF, 0x00D5, 0x006C, 0x005B, 0x0019, 0x0075, 0x001C, 0x00EA,
0x0A7C, 0x0002, 0x0075, 0x00F5, 0x00CB, 0x0A25, 0x0AC6, 0x005C,
0x00BA, 0x0A80, 0x00C6, 0x0ADA, 0x0A40, 0x0059, 0x0094, 0x0A08,
0x0053, 0x0098, 0x00FD, 0x0096, 0x0AB8, 0x0ADA, 0x0023, 0x0060,
0x0A6A, 0x00CB, 0x0AB2, 0x0A25, 0x003B, 0x004F, 0x0A4D, 0x000B,
0x002A, 0x00D1, 0x00E0, 0x00AF, 0x006D, 0x00B3, 0x00CB, 0x0072,
0x00BE, 0x0007, 0x00AC, 0x00AE, 0x000B, 0x0039, 0x0026, 0x0005,
0x000A, 0x00B4, 0x0BD9, 0x0BEC, 0x0061, 0x0024, 0x00E0, 0x007B,
0x0031, 0x004B, 0x005E, 0x0022, 0x0B8A, 0x00AD, 0x000B, 0x000C,
0x008D, 0x0A23, 0x0A22, 0x00B0, 0x00F5, 0x0ADD, 0x0044, 0x0ADD,
0x0ADD, 0x006F, 0x00F3, 0x0A22, 0x009A, 0x00F5, 0x000C, 0x0030,
0x0ADE, 0x0ADE, 0x0003, 0x00F4, 0x0A21, 0x001B, 0x0A21, 0x0ADF,
0x00AA, 0x000C, 0x0ADE, 0x0042, 0x00F4, 0x00F2, 0x005C, 0x00EF,
0x0011, 0x007E, 0x000B, 0x0012, 0x0093, 0x00ED, 0x00EC, 0x0075,
0x00F2, 0x0011, 0x0039, 0x000B, 0x000C, 0x00C5, 0x0BFE, 0x0BFF,
0x0017, 0x00F5, 0x0012, 0x00A0, 0x0012, 0x0012, 0x00E4, 0x00F3,
0x0BFF, 0x00E6, 0x00F5, 0x000C, 0x00FF, 0x0ADD, 0x0ADD, 0x00E7,
0x00F4, 0x0A20, 0x00EF, 0x0A20, 0x0ADE, 0x007E, 0x000C, 0x0ADD,
0x0081, 0x00F4, 0x00F2, 0x00E5, 0x0A21, 0x0ADF, 0x00F3, 0x000B,
0x0AE0, 0x00F3, 0x0A1F, 0x0A1E, 0x004F, 0x00F2, 0x0ADF, 0x00BB,
0x000B, 0x000C, 0x009A, 0x00EE, 0x00EF, 0x0038, 0x00F5, 0x0012,
0x000C, 0x0012, 0x0012, 0x00CB, 0x00F3, 0x00EF, 0x00E5, 0x00F5,
0x000C, 0x0032, 0x0B02, 0x0B02, 0x0089, 0x00F4, 0x00EC, 0x0088,
0x00EC, 0x0012, 0x0086, 0x000C, 0x0B02, 0x004A, 0x00F4, 0x00F2,
0x00F2, 0x0A20, 0x0ADE, 0x00C7, 0x000B, 0x0ADF, 0x001C, 0x0A20,
0x0A21, 0x0088, 0x00F2, 0x0ADE, 0x002A, 0x000B, 0x000C, 0x00C9,
0x0A1F, 0x0A1E, 0x007F, 0x00F5, 0x0AE1, 0x00BC, 0x0AE1, 0x0AE1,
0x0075, 0x00F3, 0x0A1E, 0x00E9, 0x00F5, 0x000C, 0x0081, 0x0011,
0x0011, 0x00E2, 0x00F4, 0x00EC, 0x00CD, 0x00EC, 0x0012, 0x00B3,
0x000C, 0x0011, 0x00BA, 0x00F4, 0x00F2, 0x00BA, 0x0BFD, 0x0B03,
0x00FF, 0x000B, 0x0012, 0x0034, 0x00ED, 0x00EC, 0x007A, 0x00F2,
0x0B03, 0x0042, 0x000B, 0x000C, 0x00E3, 0x0A20, 0x0A21, 0x0097,
0x00F5, 0x0AE0, 0x00D1, 0x0AE0, 0x0AE0, 0x00D6, 0x00F3, 0x0A21,
0x00CA, 0x00F5, 0x000C, 0x000C, 0x0AE1, 0x0AE1, 0x00B1, 0x00F4,
0x0A1C, 0x000D, 0x0A1C, 0x0AE2, 0x0096, 0x000C, 0x0AE1, 0x0020,
0x00F4, 0x00F2, 0x003C, 0x00EF, 0x0011, 0x003B, 0x000B, 0x0012,
0x003B, 0x00ED, 0x00EC, 0x003E, 0x00F2, 0x0011, 0x0003, 0x000B,
0x000C, 0x00F8, 0x0BFB, 0x0BFA, 0x00E5, 0x00F5, 0x0012, 0x00DC,
0x0012, 0x0012, 0x00C1, 0x00F3, 0x0BFA, 0x0083, 0x00F5, 0x000C,
0x0021, 0x0AE0, 0x0AE0, 0x00DF, 0x00F4, 0x0A1F, 0x00AE, 0x0A1F,
0x0AE1, 0x008E, 0x000C, 0x0AE0, 0x008E, 0x00F4, 0x00F2, 0x00D9,
0x0A1C, 0x0AE2, 0x001E, 0x000B, 0x0AE3, 0x006A, 0x0A1C, 0x0A1D,
0x000E, 0x000C, 0x0AE2, 0x00B1, 0x00F4, 0x00F2, 0x0055, 0x00EF,
0x0011, 0x00F4, 0x000B, 0x0012, 0x00A3, 0x00ED, 0x00EC, 0x00A6,
0x00F2, 0x0011, 0x00BB, 0x000B, 0x000C, 0x00D0, 0x0BFA, 0x0BFB,
0x0086, 0x00F5, 0x0012, 0x00FF, 0x0012, 0x0012, 0x00F8, 0x00F3,
0x0BFB, 0x007A, 0x00F5, 0x000C, 0x006B, 0x0AE1, 0x0AE1, 0x0073,
0x00F4, 0x0A1C, 0x0001, 0x0A1C, 0x0AE2, 0x003C, 0x000C, 0x0AE1,
0x0058, 0x00F4, 0x00F2, 0x0047, 0x0A1D, 0x0AE3, 0x0027, 0x000B,
0x0AE4, 0x00CB, 0x0A1B, 0x0A1A, 0x00CE, 0x00F2, 0x0AE3, 0x001D,
0x000B, 0x000C, 0x004C, 0x00EE, 0x00EF, 0x00F5, 0x00F5, 0x0012,
0x000A, 0x0012, 0x0012, 0x000C, 0x00F3, 0x00EF, 0x00D2, 0x00F5,
0x000C, 0x00F2, 0x0B06, 0x0B06, 0x00EB, 0x00F4, 0x00EC, 0x00E9,
0x00EC, 0x0012, 0x0045, 0x000C, 0x0B06, 0x00A2, 0x00F4, 0x00F2,
0x0025, 0x0A1C, 0x0AE2, 0x0094, 0x000B, 0x0AE3, 0x000D, 0x0A1C,
0x0A1D, 0x000E, 0x000C, 0x0AE2, 0x0009, 0x00F4, 0x00F2, 0x0013,
0x0AE4, 0x0AE4, 0x000E, 0x00F4, 0x0A1B, 0x0009, 0x0AE5, 0x0AE5,
0x0009, 0x00F3, 0x0A1A, 0x000E, 0x000B, 0x000C, 0x0017, 0x00EE,
0x00EF, 0x0009, 0x000B, 0x0012, 0x000E, 0x00ED, 0x00EC, 0x000E,
0x000C, 0x0011, 0x0009, 0x00F4, 0x00F2, 0x0010, 0x0B07, 0x0B07,
0x000E, 0x00F4, 0x00EC, 0x0009, 0x0012, 0x0012, 0x0009, 0x00F3,
0x0BF9, 0x000E, 0x000B, 0x000C, 0x0016, 0x0A1C, 0x0A1D, 0x0009,
0x000B, 0x0AE4, 0x000E, 0x0A1B, 0x0A1A, 0x000E, 0x000C, 0x0AE3,
0x0009, 0x00F4, 0x00F2, 0x0013, 0x0AE5, 0x0AE5, 0x000E, 0x00F4,
0x0A18, 0x0009, 0x0AE6, 0x0AE6, 0x0009, 0x00F3, 0x0A1B, 0x000E,
0x000B, 0x000C, 0x0017, 0x00EE, 0x00EF, 0x0009, 0x000B, 0x0012,
0x000E, 0x00ED, 0x00EC, 0x000E, 0x000C, 0x0011, 0x0009, 0x00F4,
0x00F2, 0x0010, 0x0B08, 0x0B08, 0x000E, 0x00F4, 0x00EC, 0x0009,
0x0012, 0x0012, 0x0009, 0x00F3, 0x0BF6, 0x000E, 0x000B, 0x000C,
0x0016, 0x0A1B, 0x0A1A, 0x0009, 0x000B, 0x0AE5, 0x000E, 0x0A1A,
0x0A1B, 0x000E, 0x000C, 0x0AE4, 0x0009, 0x00F4, 0x00F2, 0x0013,
0x0AE6, 0x0AE6, 0x000E, 0x00F4, 0x0A19, 0x0009, 0x0AE7, 0x0AE7,
0x0009, 0x00F3, 0x0A18, 0x000E, 0x000B, 0x000C, 0x0017, 0x00EE,
0x00EF, 0x0009, 0x000B, 0x0012, 0x000E, 0x00ED, 0x00EC, 0x000E,
0x000C, 0x0011, 0x0009, 0x00F4, 0x00F2, 0x0010, 0x0B09, 0x0B09,
0x000E, 0x00F4, 0x00EC, 0x0009, 0x0012, 0x0012, 0x0009, 0x00F3,
0x0BF7, 0x000E, 0x000B, 0x000C, 0x0016, 0x0A1A, 0x0A1B, 0x0009,
0x000B, 0x0AE6, 0x000E, 0x0A19, 0x0A18, 0x000E, 0x000C, 0x0AE5,
0x0009, 0x00F4, 0x00F2, 0x0013, 0x0AE7, 0x0AE7, 0x000E, 0x00F4,
0x0A16, 0x0009, 0x0AE8, 0x0AE8, 0x0009, 0x00F3, 0x0A19, 0x000E,
0x000B, 0x000C, 0x0017, 0x00EE, 0x00EF, 0x0009, 0x000B, 0x0012,
0x000E, 0x00ED, 0x00EC, 0x000E, 0x000C, 0x0011, 0x0009, 0x00F4,
0x00F2, 0x0010, 0x0B0A, 0x0B0A, 0x000E, 0x00F4, 0x00EC, 0x0009,
0x0012, 0x0012, 0x0009, 0x00F3, 0x0BF4, 0x000E, 0x000B, 0x000C,
0x0016, 0x0A19, 0x0A18, 0x0009, 0x000B, 0x0AE7, 0x000E, 0x0A18,
0x0A19, 0x000E, 0x000C, 0x0AE6, 0x0009, 0x00F4, 0x00F2, 0x0013,
0x0AE8, 0x0AE8, 0x000E, 0x00F4, 0x0A17, 0x0009, 0x0AE9, 0x0AE9,
0x0009, 0x00F3, 0x0A16, 0x000E, 0x000B, 0x000C, 0x0017, 0x00EE,
0x00EF, 0x0009, 0x000B, 0x0012, 0x000E, 0x00ED, 0x00EC, 0x000E,
0x000C, 0x0011, 0x0009, 0x00F4, 0x00F2, 0x0010, 0x0B0B, 0x0B0B,
0x000E, 0x00F4, 0x00EC, 0x0009, 0x0012, 0x0012, 0x0009, 0x00F3,
0x0BF5, 0x000E, 0x000B, 0x000C, 0x0016, 0x0A18, 0x0A19, 0x0009,
0x000B, 0x0AE8, 0x000E, 0x0A17, 0x0A16, 0x000E, 0x000C, 0x0AE7,
0x0009, 0x00F4, 0x00F2, 0x0013, 0x0AE9, 0x0AE9, 0x000E, 0x00F4,
0x0A14, 0x0009, 0x0AEA, 0x0AEA, 0x0009, 0x00F3, 0x0A17, 0x000E,
0x000B, 0x000C, 0x0017, 0x00EE, 0x00EF, 0x0009, 0x000B, 0x0012,
0x000E, 0x00ED, 0x00EC, 0x000E, 0x000C, 0x0011, 0x0009, 0x00F4,
0x00F2, 0x0010, 0x0B0C, 0x0B0C, 0x000E, 0x00F4, 0x00EC, 0x0009,
0x0012, 0x0012, 0x0009, 0x00F3, 0x0BF2, 0x000E, 0x000B, 0x000C,
0x0016, 0x0A17, 0x0A16, 0x0009, 0x000B, 0x0AE9, 0x000E, 0x0A16,
0x0A17, 0x000E, 0x000C, 0x0AE8, 0x0009, 0x00F4, 0x00F2, 0x0013,
0x0AEA, 0x0AEA, 0x000E, 0x00F4, 0x0A15, 0x0009, 0x0AEB, 0x0AEB,
0x0009, 0x00F3, 0x0A14, 0x000E, 0x000B, 0x000C, 0x0017, 0x00EE,
0x00EF, 0x0009, 0x000B, 0x0012, 0x000E, 0x00ED, 0x00EC, 0x000E,
0x000C, 0x0011, 0x0009, 0x00F4, 0x00F2, 0x0010, 0x0B0D, 0x0B0D,
0x000E, 0x00F4, 0x00EC, 0x0009, 0x0012, 0x0012, 0x0009, 0x00F3,
0x0BF3, 0x000E, 0x000B, 0x000C, 0x0016, 0x0A16, 0x0A17, 0x0009,
0x000B, 0x0AEA, 0x000E, 0x0A15, 0x0A14, 0x000E, 0x000C, 0x0AE9,
0x0009, 0x00F4, 0x00F2, 0x0013, 0x0AEB, 0x0AEB, 0x000E, 0x00F4,
0x0A12, 0x0009, 0x0AEC, 0x0AEC, 0x0009, 0x00F3, 0x0A15, 0x000E,
0x000B, 0x000C, 0x0017, 0x00EE, 0x00EF, 0x0009, 0x000B, 0x0012,
0x000E, 0x00ED, 0x00EC, 0x000E, 0x000C, 0x0011, 0x0009, 0x00F4,
0x00F2, 0x0010, 0x0B0E, 0x0B0E, 0x000E, 0x00F4, 0x00EC, 0x0009,
0x0012, 0x0012, 0x0009, 0x00F3, 0x0BF0, 0x000E, 0x000B, 0x000C,
0x0016, 0x0A15, 0x0A14, 0x0009, 0x000B, 0x0AEB, 0x000E, 0x0A14,
0x0A15, 0x000E, 0x000C, 0x0AEA, 0x0009, 0x00F4, 0x00F2, 0x0013,
0x0AEC, 0x0AEC, 0x000E, 0x00F4, 0x0A13, 0x0009, 0x0AED, 0x0AED,
0x0009, 0x00F3, 0x0A12, 0x000E, 0x000B, 0x000C, 0x0017, 0x00EE,
0x00EF, 0x0009, 0x000B, 0x0012, 0x000E, 0x00ED, 0x00EC, 0x000E,
0x000C, 0x0011, 0x0009, 0x00F4, 0x00F2, 0x0010, 0x0B0F, 0x0B0F,
0x000E, 0x00F4, 0x00EC, 0x0009, 0x0012, 0x0012, 0x0009, 0x00F3,
0x0BF1, 0x000E, 0x000B, 0x000C, 0x0016, 0x0A14, 0x0A15, 0x0009,
0x000B, 0x0AEC, 0x000E, 0x0A13, 0x0A12, 0x000E, 0x000C, 0x0AEB,
0x0009, 0x00F4, 0x00F2, 0x0013, 0x0AED, 0x0AED, 0x000E, 0x00F4,
0x0A10, 0x0009, 0x0AEE, 0x0AEE, 0x0009, 0x00F3, 0x0A13, 0x000E,
0x000B, 0x000C, 0x0017, 0x00EE, 0x00EF, 0x0009, 0x000B, 0x0012,
0x000E, 0x00ED, 0x00EC, 0x000E, 0x000C, 0x0011, 0x0009, 0x00F4,
0x00F2, 0x0010, 0x0B10, 0x0B10, 0x000E, 0x00F4, 0x00EC, 0x0009,
0x0012, 0x0012, 0x0009, 0x00F3, 0x0BEE, 0x000E, 0x000B, 0x000C,
0x0016, 0x0A13, 0x0A12, 0x0009, 0x000B, 0x0AED, 0x000E, 0x0A12,
0x0A13, 0x000E, 0x000C, 0x0AEC, 0x0009, 0x00F4, 0x00F2, 0x0013,
0x0AEE, 0x0AEE, 0x000E, 0x00F4, 0x0A11, 0x0009, 0x0AEF, 0x0AEF,
0x0009, 0x00F3, 0x0A10, 0x000E, 0x000B, 0x000C, 0x0017, 0x00EE,
0x00EF, 0x0009, 0x000B, 0x0012, 0x000E, 0x00ED, 0x00EC, 0x000E,
0x000C, 0x0011, 0x0009, 0x00F4, 0x00F2, 0x0010, 0x0B11, 0x0B11,
0x000E, 0x00F4, 0x00EC, 0x0009, 0x0012, 0x0012, 0x0009, 0x00F3,
0x0BEF, 0x000E, 0x000B, 0x000C, 0x0016, 0x0A12, 0x0A13, 0x0009,
0x000B, 0x0AEE, 0x000E, 0x0A11, 0x0A10, 0x000E, 0x000C, 0x0AED,
0x0009, 0x00F4, 0x00F2, 0x0013, 0x0AEF, 0x0AEF, 0x000E, 0x00F4,
0x0A0E, 0x0009, 0x0AF0, 0x0AF0, 0x0009, 0x00F3, 0x0A11, 0x000E,
0x000B, 0x000C, 0x0017, 0x00EE, 0x00EF, 0x0009, 0x000B, 0x0012,
0x000E, 0x00ED, 0x00EC, 0x000E, 0x000C, 0x0011, 0x0009, 0x00F4,
0x00F2, 0x0010, 0x0B12, 0x0B12, 0x000E, 0x00F4, 0x00EC, 0x0009,
0x0012, 0x0012, 0x0009, 0x00F3, 0x0BEC, 0x000E, 0x000B, 0x000C,
0x0016, 0x0A11, 0x0A10, 0x0009, 0x000B, 0x0AEF, 0x000E, 0x0A10,
0x0A11, 0x000E, 0x000C, 0x0AEE, 0x0009, 0x00F4, 0x00F2, 0x0013,
0x0AF0, 0x0AF0, 0x000E, 0x00F4, 0x0A0F, 0x0009, 0x0AF1, 0x0AF1,
0x0009, 0x00F3, 0x0A0E, 0x000E, 0x000B, 0x000C, 0x0017, 0x00EE,
0x00EF, 0x0009, 0x000B, 0x0012, 0x000E, 0x00ED, 0x00EC, 0x000E,
0x000C, 0x0011, 0x0009, 0x00F4, 0x00F2, 0x0010, 0x0B13, 0x0B13,
0x000E, 0x00F4, 0x00EC, 0x0009, 0x0012, 0x0012, 0x0009, 0x00F3,
0x0BED, 0x000E, 0x000B, 0x000C, 0x0016, 0x0A10, 0x0A11, 0x0009,
0x000B, 0x0AF0, 0x000E, 0x0A0F, 0x0A0E, 0x000E, 0x000C, 0x0AEF,
0x0009, 0x00F4, 0x00F2, 0x0013, 0x0AF1, 0x0AF1, 0x000E, 0x00F4,
0x0A0C, 0x0009, 0x0AF2, 0x0AF2, 0x0009, 0x00F3, 0x0A0F, 0x000E,
0x000B, 0x000C, 0x0017, 0x00EE, 0x00EF, 0x0009, 0x000B, 0x0012,
0x000E, 0x00ED, 0x00EC, 0x000E, 0x000C, 0x0011, 0x0009, 0x00F4,
0x00F2, 0x0010, 0x0B14, 0x0B14, 0x000E, 0x00F4, 0x00EC, 0x0009,
0x0012, 0x0012, 0x0009, 0x00F3, 0x0BEA, 0x000E, 0x000B, 0x000C,
0x0016, 0x0A0F, 0x0A0E, 0x0009, 0x000B, 0x0AF1, 0x000E, 0x0A0E,
0x0A0F, 0x000E, 0x000C, 0x0AF0, 0x0009, 0x00F4, 0x00F2, 0x0013,
0x0AF2, 0x0AF2, 0x000E, 0x00F4, 0x0A0D, 0x0009, 0x0AF3, 0x0AF3,
0x0009, 0x00F3, 0x0A0C, 0x000E, 0x000B, 0x000C, 0x0017, 0x00EE,
0x00EF, 0x0009, 0x000B, 0x0012, 0x000E, 0x00ED, 0x00EC, 0x000E,
0x000C, 0x0011, 0x0009, 0x00F4, 0x00F2, 0x0010, 0x0B15, 0x0B15,
0x000E, 0x00F4, 0x00EC, 0x0009, 0x0012, 0x0012, 0x0009, 0x00F3,
0x0BEB, 0x000E, 0x000B, 0x000C, 0x0016, 0x0A0E, 0x0A0F, 0x0009,
0x000B, 0x0AF2, 0x000E, 0x0A0D, 0x0A0C, 0x000E, 0x000C, 0x0AF1,
0x0009, 0x00F4, 0x00F2, 0x0013, 0x0AF3, 0x0AF3, 0x000E, 0x00F4,
0x0A0A, 0x0009, 0x0AF4, 0x0AF4, 0x0009, 0x00F3, 0x0A0D, 0x000E,
0x000B, 0x000C, 0x0017, 0x00EE, 0x00EF, 0x0009, 0x000B, 0x0012,
0x000E, 0x00ED, 0x00EC, 0x000E, 0x000C, 0x0011, 0x0009, 0x00F4,
0x00F2, 0x0010, 0x0B16, 0x0B16, 0x000E, 0x00F4, 0x00EC, 0x0009,
0x0012, 0x0012, 0x0009, 0x00F3, 0x0BE8, 0x000E, 0x000B, 0x000C,
0x0016, 0x0A0D, 0x0A0C, 0x0009, 0x000B, 0x0AF3, 0x000E, 0x0A0C,
0x0A0D, 0x000E, 0x000C, 0x0AF2, 0x0009, 0x00F4, 0x00F2, 0x0013,
0x0AF4, 0x0AF4, 0x000E, 0x00F4, 0x0A0B, 0x0009, 0x0AF5, 0x0AF5,
0x0009, 0x00F3, 0x0A0A, 0x000E, 0x000B, 0x000C, 0x0017, 0x00EE,
0x00EF, 0x0009, 0x000B, 0x0012, 0x000E, 0x00ED, 0x00EC, 0x000E,
0x000C, 0x0011, 0x0009, 0x00F4, 0x00F2, 0x0010, 0x0B17, 0x0B17,
0x000E, 0x00F4, 0x00EC, 0x0009, 0x0012, 0x0012, 0x0009, 0x00F3,
0x0BE9, 0x000E, 0x000B, 0x000C, 0x0016, 0x0A0C, 0x0A0D, 0x0009,
0x000B, 0x0AF4, 0x000E, 0x0A0B, 0x0A0A, 0x000E, 0x000C, 0x0AF3,
0x0009, 0x00F4, 0x00F2, 0x0013, 0x0AF5, 0x0AF5, 0x000E, 0x00F4,
0x0A08, 0x0009, 0x0AF6, 0x0AF6, 0x0009, 0x00F3, 0x0A0B, 0x000E,
0x000B, 0x000C, 0x0017, 0x00EE, 0x00EF, 0x0009, 0x000B, 0x0012,
0x000E, 0x00ED, 0x00EC, 0x000E, 0x000C, 0x0011, 0x0009, 0x00F4,
0x00F2, 0x0010, 0x0B18, 0x0B18, 0x000E, 0x00F4, 0x00EC, 0x0009,
0x0012, 0x0012, 0x0009, 0x00F3, 0x0BE6, 0x000E, 0x000B, 0x000C,
0x0016, 0x0A0B, 0x0A0A, 0x0009, 0x000B, 0x0AF5, 0x000E, 0x0A0A,
0x0A0B, 0x000E, 0x000C, 0x0AF4, 0x0009, 0x00F4, 0x00F2, 0x0013,
0x0AF6, 0x0AF6, 0x000E, 0x00F4, 0x0A09, 0x0009, 0x0AF7, 0x0AF7,
0x0009, 0x00F3, 0x0A08, 0x000E, 0x000B, 0x000C, 0x0017, 0x00EE,
0x00EF, 0x0009, 0x000B, 0x0012, 0x000E, 0x00ED, 0x00EC, 0x000E,
0x000C, 0x0011, 0x0009, 0x00F4, 0x00F2, 0x0010, 0x0B19, 0x0B19,
0x000E, 0x00F4, 0x00EC, 0x0009, 0x0012, 0x0012, 0x0009, 0x00F3,
0x0BE7, 0x000E, 0x000B, 0x000C, 0x0016, 0x0A0A, 0x0A0B, 0x0009,
0x000B, 0x0AF6, 0x000E, 0x0A09, 0x0A08, 0x000E, 0x000C, 0x0AF5,
0x0009, 0x00F4, 0x00F2, 0x0013, 0x0AF7, 0x0AF7, 0x000E, 0x00F4,
0x0A06, 0x0009, 0x0AF8, 0x0AF8, 0x0009, 0x00F3, 0x0A09, 0x000E,
0x000B, 0x000C, 0x0017, 0x00EE, 0x00EF, 0x0009, 0x000B, 0x0012,
0x000E, 0x00ED, 0x00EC, 0x000E, 0x000C, 0x0011, 0x0009, 0x00F4,
0x00F2, 0x0010, 0x0B1A, 0x0B1A, 0x000E, 0x00F4, 0x00EC, 0x0009,
0x0012, 0x0012, 0x0009, 0x00F3, 0x0BE4, 0x000E, 0x000B, 0x000C,
0x0016, 0x0A09, 0x0A08, 0x0009, 0x000B, 0x0AF7, 0x000E, 0x0A08,
0x0A09, 0x000E, 0x000C, 0x0AF6, 0x0009, 0x00F4, 0x00F2, 0x0013,
0x0AF8, 0x0AF8, 0x000E, 0x00F4, 0x0A2A, 0x0009, 0x0AD4, 0x0AD4,
0x0009, 0x00F3, 0x0A06, 0x000E, 0x000B, 0x000C, 0x0017, 0x00EE,
0x00EF, 0x0009, 0x000B, 0x0012, 0x000E, 0x00ED, 0x00EC, 0x000E,
0x000C, 0x0011, 0x0009, 0x00F4, 0x00F2, 0x0010, 0x0B1B, 0x0B1B,
0x000E, 0x00F4, 0x00EC, 0x0009, 0x0012, 0x0012, 0x0009, 0x00F3,
0x0BE5, 0x000E, 0x000B, 0x000C, 0x0016, 0x0A08, 0x0A09, 0x0009,
0x000B, 0x0AF8, 0x000E, 0x0A07, 0x0A06, 0x000E, 0x000C, 0x0AF7,
0x0009, 0x00F4, 0x00F2, 0x0013, 0x0AD4, 0x0AD4, 0x000E, 0x00F4,
0x0A2B, 0x0009, 0x0AD5, 0x0AD5, 0x0009, 0x00F3, 0x0A2A, 0x000E,
0x000B, 0x000C, 0x0017, 0x00EE, 0x00EF, 0x0009, 0x000B, 0x0012,
0x000E, 0x00ED, 0x00EC, 0x000E, 0x000C, 0x0011, 0x0009, 0x00F4,
0x00F2, 0x0010, 0x0B1C, 0x0B1C, 0x000E, 0x00F4, 0x00EC, 0x0009,
0x0012, 0x0012, 0x0009, 0x00F3, 0x0BE2, 0x000E, 0x000B, 0x000C,
0x0016, 0x0A07, 0x0A06, 0x0009, 0x000B, 0x0AD4, 0x000E, 0x0A2B,
0x0A2A, 0x000E, 0x000C, 0x0AF8, 0x0009, 0x00F4, 0x00F2, 0x0013,
0x0AD5, 0x0AD5, 0x000E, 0x00F4, 0x0A28, 0x0009, 0x0AD6, 0x0AD6,
0x0009, 0x00F3, 0x0A2B, 0x000E, 0x000B, 0x000C, 0x0017, 0x00EE,
0x00EF, 0x0009, 0x000B, 0x0012, 0x000E, 0x00ED, 0x00EC, 0x000E,
0x000C, 0x0011, 0x0009, 0x00F4, 0x00F2, 0x0010, 0x0B1D, 0x0B1D,
0x000E, 0x00F4, 0x00EC, 0x0009, 0x0012, 0x0012, 0x0009, 0x00F3,
0x0BE3, 0x000E, 0x000B, 0x000C, 0x0016, 0x00F5, 0x00F4, 0x0002,
0x0000, 0x0000, 0x0000, 0x0000, 0x0000, 0x0000, 0x0049, 0x006E,
0x0070, 0x0075, 0x0074, 0x003A
};
unsigned short data[74] = {
0x009E, 0x0028, 0x00F5, 0x0075, 0x0073, 0x0073, 0x0030, 0x007E,
0x0048, 0x0048, 0x00F2, 0x002F, 0x003D, 0x00EC, 0x0001, 0x0026,
0x003E, 0x00CD, 0x0082, 0x00AD, 0x00B1, 0x00D1, 0x0036, 0x00D2,
0x00B4, 0x00E5, 0x00E8, 0x004C, 0x003D, 0x000C, 0x0073, 0x00FD,
0x0059, 0x00A7, 0x0048, 0x0093, 0x00FD, 0x0006, 0x00E0, 0x0044,
0x0048, 0x0071, 0x0094, 0x004A, 0x008E, 0x00A4, 0x0036, 0x0091,
0x0023, 0x00EE, 0x0068, 0x00C1, 0x005D, 0x000B, 0x004D, 0x001A,
0x0074, 0x0083, 0x0051, 0x0052, 0x00EE, 0x00FE, 0x0011, 0x00A2,
0x00A1, 0x0064, 0x00BD, 0x0098, 0x004D, 0x00B9, 0x0097, 0x0045,
0x00E6, 0x00F7
};
unsigned char s[256];
char* get_name(int id) {
char* p = (char*)malloc(0x100);
if (id >= 2772) {
snprintf(p, 0x100, "data[%d]", id - 2772);
}
else {
snprintf(p, 0x100, "op[%d]", id);
}
return p;
}
void __cdecl rc4_key(_BYTE* a1, const char* a2, unsigned int a3)
{
int v3;
char v4;
int i;
int j;
char v7[256];
v3 = 0;
memset(v7, 0, sizeof(v7));
for (i = 0; i < 256; ++i)
{
a1[i] = i;
v7[i] = a2[i % a3];
}
for (j = 0; j < 256; ++j)
{
v3 = ((unsigned __int8)v7[j] + v3 + (unsigned __int8)a1[j]) % 256;
v4 = a1[j];
a1[j] = a1[v3];
a1[v3] = v4;
}
}
unsigned int __cdecl rc4(unsigned __int8* s, _WORD* data, unsigned int len)
{
unsigned int result;
int v4;
unsigned int i;
int v6;
unsigned __int8 v7;
v6 = 0;
v4 = 0;
for (i = 0; i < len; ++i)
{
v6 = (v6 + 1) % 256;
v4 = (v4 + s[v6]) % 256;
v7 = s[v6];
s[v6] = s[v4];
s[v4] = v7;
data[i] ^= s[(s[v4] + s[v6]) % 256];
result = i + 1;
}
return result;
}
int main() {
rc4_key(s, "YunZh1JunAlkaid", 0xF);
rc4(s, data, 0x4Au);
int v4;
int v5 = 0;
while ((unsigned __int16)op[0] != 0xFFFF)
{
if (op[2] == 1)
{
op[2] = 0;
printf("%c", op[3]);
}
if (op[7] == 1)
{
op[7] = 0;
scanf_s("%c", &op[8]);
v4 = v5++;
if (v4 == 36 && op[8] != 0x7E)
{
puts("Wrong!");
return 0;
}
if (v4 == 36) {
printf("---------------End Input---------------\n");
int i;
}
}
if (op[19])
{
int i;
puts("Wrong!");
return 0;
}
unsigned __int16 v9 = op[0];
rc4(s, &op[(unsigned __int16)op[0]], 3);
unsigned __int16 v7 = op[v9];
unsigned __int16 v8 = op[v9 + 1];
unsigned __int16 v6 = op[v9 + 2];
op[0] = v9 + 3;
rc4(s, &op[v9], 3);
op[v6] = ~(op[v7] & op[v8]);
printf("%s = ~(%s & %s)\n", get_name(v6), get_name(v7), get_name(v8));
}
return 0;
}
|