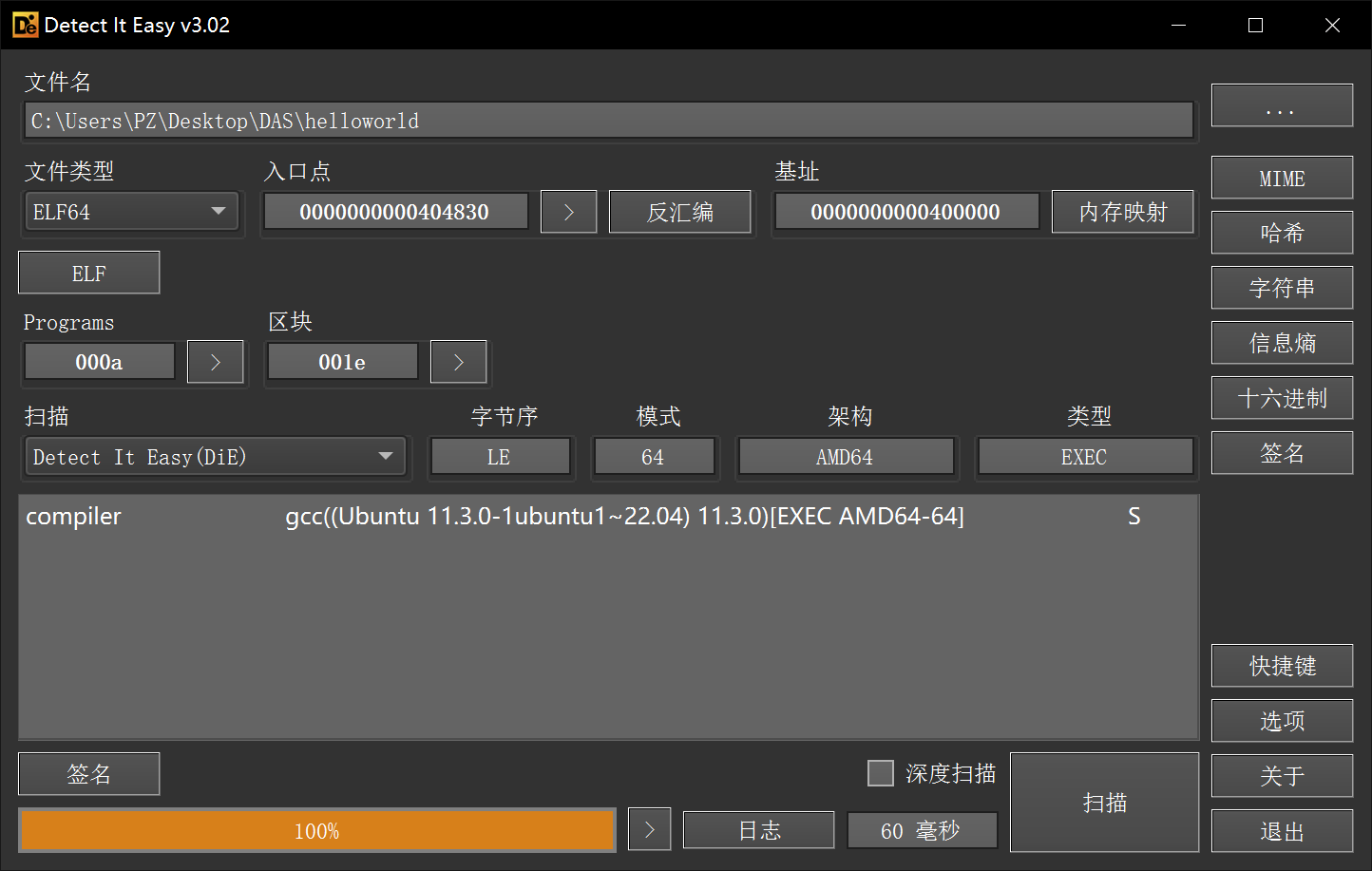
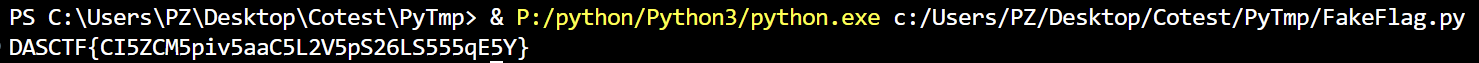
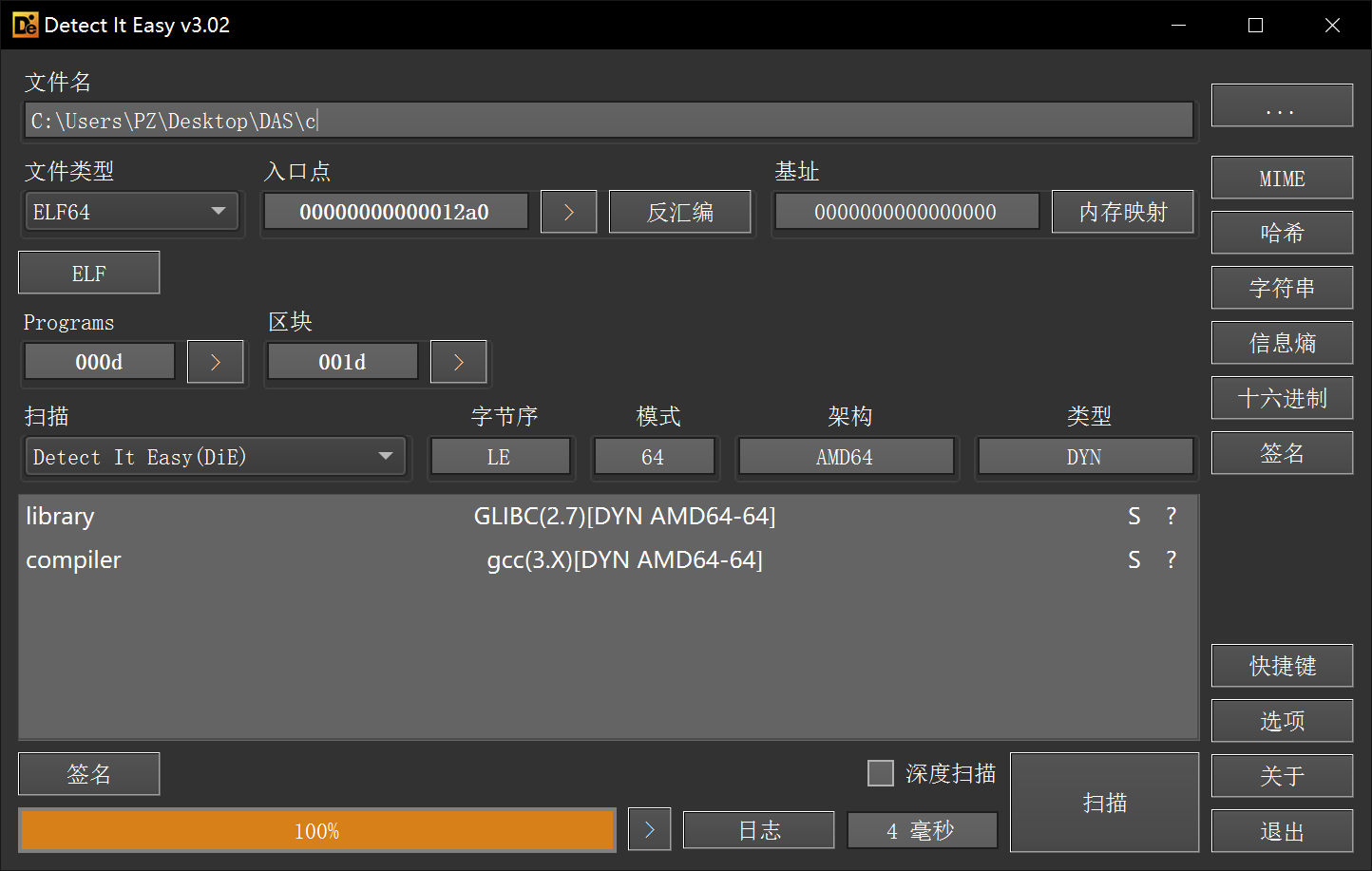
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
| from Crypto.Util.number import *
import gmpy2 as gp
n=0x1DE0B6B3A76408FC69F3467E8F0CE5F
p=1152921504606848051
q=2152921504606847269
e=0x10001
d=gp.invert(e,(p-1)*(q-1))
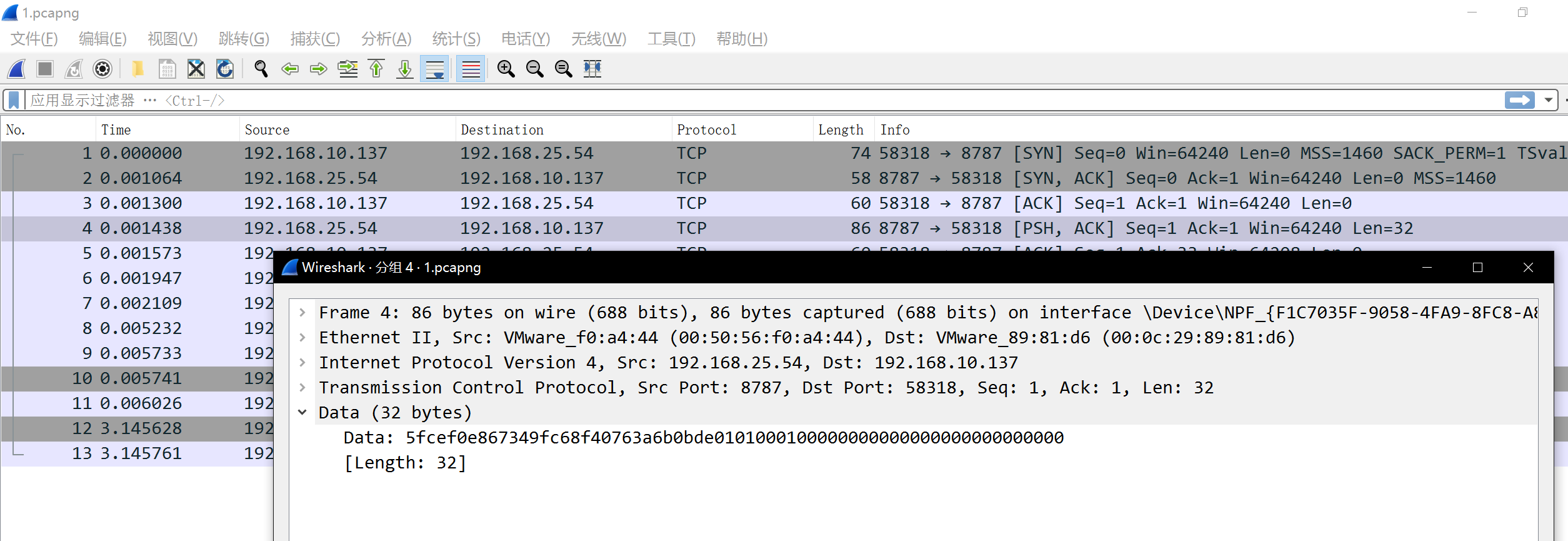
data="7a3202cc78acb66216341041b18ea201a3eb93301b27a2b6e77cb244d2e02c0082cd6369f3a7c1d2a1dd9b561c98510017c911f2ac5ec565e2d9b9016df34900661212d889172b99954d25018b5d43012e81783c2d8cebedeb053ccd651de400"
k=b""
for i in range(0,len(data),32):
c=bytes.fromhex(data[i:i+32])[::-1]
c=int(c.hex(),16)
k+=long_to_bytes(pow(c,d,n))
print(long_to_bytes(pow(c,d,n)))
"""
databuf : DWORD *4 BYTE[16]
"""
teak=[int.from_bytes(k[i:i+8],"little") for i in range(0,32,8)]
for i in teak:
print(hex(i),end=',')
print()
s="16cb56c17a19fb2ddcdb8472d52d1d6b1693164a13316a33be05bc1c4a2029b9efbf96dc917da5056d3ee46c2b0815cb56c17b19fb2de6db847211fd382bc3eb739037f7dfa4b0ca553f4dc67f81b71b7f9215cb56c17819fb2dd6db84727c8526cc3d6383bbcf0159590648586e7dd08b49cc1ee7f519ec206592254842b7f33d25646640ab16cb56c17a19fb2de5db8472c008ba6c15334f76485d8c17082f4468addbb3a62d20e754105d1014cb56c17a19fb2dfedb847215cb56c17219fb2dbdd984723419b3ea63306ff1224173d834b1f9c436332f39ec2aa102bb7747859d50793674b05a56f14ee29491895944cbf1f6846a9831f8dd5666202c4b0d558a690239b1dece4322fe535c0742cc2f37378577b999eaab713d853643bc379dac7f7f471ef2240b8898fac4431149aa27a65507db39a9111dea802a803506fbd4a2d558068974f993dcab4587a5620db6909a951dcf8bb65d4f8e92ac8300fd049bb3218199705babb255e7daef40a28c1d7e3f74cb1d44687be127258aafc4dbdaf09266daa68605e250aa244c179d759d22e90ed3d8a9bf155fae86c721ed8ee5603c4613ac47e5a80079b909727277fff31d20529b3c022e3b1a3616d639ca036586ef17d3dc9bdf1eeec5859f0022514f29b240f30c818e7fdd478f36779978c08885b2266e3cf599d0a4c27bca4615720a08e13916ec4a6ef5c943ddb25566e620726f56c5160913564d683badcc7204ec8e7080221de325a431a0680e9e108e427c7bc3807b86c78820bc9c2340709da352d953aea805a04b53f2d88f7b8fae50e5ba2de55615bc9b2e526167226e75f5c8827593281f23a65e5098e0e8e2623ee4f892bac76e6987a05832bc0b84215bb74ed83786bd55265e61ba5702170fda63e01a44d6b8a6f1740a6c03803095e5176bde18ee873dcd6380de9f325f1c436c11e3250cebceceb319a49a4e3f2f62cfd137b602e27f3974a113df414287da48afd9e8c7ef0bdb4d345313b52d662202f543f426f8271432a20186b1dc7f70d4123def1c3745c1ffe7f4017ff60e0b7486f0e8db90889a36072583ddb26dbd37778115cb56c17e19fb2d5edb847263424fb4921f224eb2d445183f9bc6541d1ac77072a6e616e6826cbbebe96af229e79620462869e51686d4d523f782b2e5b43a769403bf62f1b87512013f95d068dc04beb337f8741b471386a7746ebc7b9c7a9568ed9b590936cdc533f6f943e3a37966362b62092ce5a3c53a95b33d0ff1ac2c5800b67b8cc40d614b8df74d4114d4bb7104b545ac7d0b9eb606578fd63561578740ce7eeaa189baacd436ae15cb56c17f19fb2d5edb8472ecc4942bbc4e2bbec5c4adb791a7096298f6347c4a277364cea894234bdcf69811f31ce644bae10edc0de4ccc200a44fa0e2faa4d2eb3b28dcecc3a468efdbfa7de2728b27dfafd1a5df4803a7986cfa768fb1f9751ba1a7d47c9a6928978810d76dceb819738f4684637d3ddd2cc41e2a4585a366d4a46b32db59508f34bf5c654be7b5c86e24cca5d1013738c32ba9b6083e76e0f93c80fe712261841e546315cb56c17c19fb2d5edb847260fd338fdcecb096e26a56603082a58f5b1fb0ffb7fc8faac33589ec52ed02256aba88b2c2836433a5d146c6efe784d47da7a7ffc4256f3dce73314c0171f89e9a4f6a95f59e8460d2b65fe178daba5faf8d34d99e32a50aefbbb7ed9c9507765958870dd2e1836fe608215ca753a7125f3cb86ac32d1149cf2a144b873fc7a96914d376ed2fe88d36a609596a68d8bb76e71d1b81a8db3618271f002ff6fb5815cb56c17d19fb2d5edb8472b72d657abc1a3c2133fa45fd834d28fce3b5bdd8f111bfa61386a306aa74598ea6e5022f4aac8d9acd442c44465eb334c26d060dfc8f4f59c13f3225a5ea111f9e3e9ef4c75f40b85c43dbdd5d30970cde507cd96fa6a88970e23c1dc1cb9a1eab2f4cc16444226aff6c49dd13e030240ea32267a1699b5b8c83d05c1cc257f5028d649e2b58d96a1f59fcd42f027179e7400f2c64c3063ae1f9c496ec019eba12cb56c17219fa2dfedb847213cb56c17919fb2dfedb847211cb56c17a19fb2dfedb8472"
cur=0
while cur<len(s):
op1 = bytearray(bytes.fromhex(s[cur:cur+24]))
cur+=24
for i in range(len(op1)):
op1[i] ^= k[i + 32]
op=[int.from_bytes(op1[i:i+4],"little") for i in range(0,12,4)]
print(op)
print(list(bytes.fromhex(s[cur:cur+2*op[-1]])))
cur+=2*op[-1]
ans6=[16,228,39,34,62,210,76,123,160,154,193,42,187,247,182,24,56,14,96,90,42,203,34,122,92,138,200,54,251,176,182,81,204,224,163,100,174,224,175,17,217,221,213,1,106,249,216,65,177,197,188,59,80,142,218,4,116,200,94,94,15,76,118,122,120,243,178,46,125,204,122,75,224,202,171,61,160,167,75,33,183,223,166,32,30,67,70,15,67,153,214,126,99,2,137,54,64,31,33,29,195,194,250,63,199,229,58,24,65,112,151,50,222,214,4,49,198,233,63,121,75,110,136,75,238,186,44,83,4,188,140,116,235,8,74,118,169,178,227,107,60,202,236,78,21,212,108,112,5,61,172,34,56,123,163,32,226,180,16,85]
ans7=[89,0,0,0,51,0,0,0,10,0,0,0,46,0,0,0,33,0,0,0,25,0,0,0,64,0,0,0,84,0,0,0,66,0,0,0,82,0,0,0,16,0,0,0,74,0,0,0,56,0,0,0,88,0,0,0,37,0,0,0,52,0,0,0,25,0,0,0,97,0,0,0,37,0,0,0,86,0,0,0,49,0,0,0,8,0,0,0,74,0,0,0,31,0,0,0,9,0,0,0,21,0,0,0,21,0,0,0,77,0,0,0,38,0,0,0,49,0,0,0,65,0,0,0,79,0,0,0,52,0,0,0,75,0,0,0,78,0,0,0,37,0,0,0,53,0,0,0,42,0,0,0,22,0,0,0,19,0,0,0]
ans8=[39,34,0,0,76,123,0,0,193,42,0,0,182,24,0,0,96,90,0,0,34,122,0,0,200,54,0,0,182,81,0,0,163,100,0,0,175,17,0,0,213,1,0,0,216,65,0,0,188,59,0,0,218,4,0,0,94,94,0,0,118,122,0,0,178,46,0,0,122,75,0,0,171,61,0,0,75,33,0,0,166,32,0,0,70,15,0,0,214,126,0,0,137,54,0,0,33,29,0,0,250,63,0,0,58,24,0,0,151,50,0,0,4,49,0,0,63,121,0,0,136,75,0,0,44,83,0,0,140,116,0,0,74,118,0,0,227,107,0,0,236,78,0,0,108,112,0,0,172,34,0,0,163,32,0,0,16,85,0,0]
ans9=[173,228,0,0,178,210,0,0,253,154,0,0,38,248,0,0,141,14,0,0,133,203,0,0,103,138,0,0,34,177,0,0,0,225,0,0,51,225,0,0,159,221,0,0,169,249,0,0,191,197,0,0,186,142,0,0,99,200,0,0,110,76,0,0,58,243,0,0,169,204,0,0,181,202,0,0,43,168,0,0,205,223,0,0,51,67,0,0,108,153,0,0,45,2,0,0,55,31,0,0,10,195,0,0,178,229,0,0,129,112,0,0,206,214,0,0,37,234,0,0,74,110,0,0,42,187,0,0,153,188,0,0,3,9,0,0,22,179,0,0,46,202,0,0,142,212,0,0,150,61,0,0,95,123,0,0,178,180,0,0]
k4=[int.from_bytes(bytes(ans6[i:i+4]),"little") for i in range(0,160,4)]
k5=[int.from_bytes(bytes(ans7[i:i+4]),"little") for i in range(0,160,4)]
k6=[int.from_bytes(bytes(ans8[i:i+4]),"little") for i in range(0,160,4)]
k7=[int.from_bytes(bytes(ans9[i:i+4]),"little") for i in range(0,160,4)]
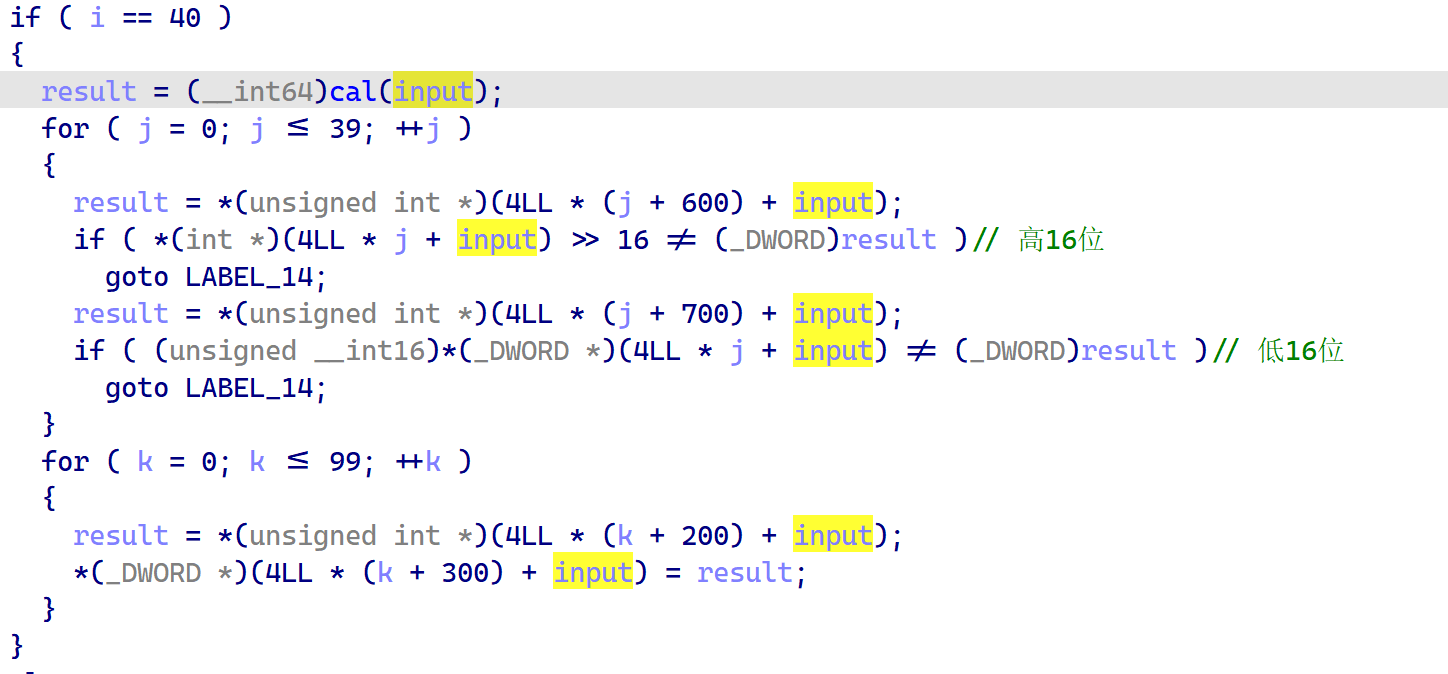
for i in range(40):
c = k7[i] | (k6[i] << 16)
c -= k5[i]
c ^= k4[i]
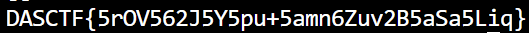
print(chr(c),end='')
|