我的upx -d怎么坏了
0x00 Routine Check Shell
upx壳,好像改了点什么,但是压缩壳只要跑起来就可以dump出来
0x01 Maze
打开主程序可以发现是迷宫题,那么直接拿到迷宫就可以走迷宫了,然而多解
0x02 Get Flag
获取迷宫发现跑出四个路径
DDDRRURURRURRRRRRDDDDRDDD
DDDRRURURRDDDLDDDDRRRRRRRUR
RRRDRRURRRRRRDDDDRDDD
RRRDRRDDDLDDDDRRRRRRRUR
后面说是最短路径,所以
1 | flag{ae2de0be8285f69db701d4dba8721a40} |
babypython
0x00 Routine Check Shell
鉴定为python字节码阅读题
0x01 GPT Time
大部分都是无用代码只有中间可用,然后直接丢到gpt翻译
1 | flag = '************************************' |
0x02 Get Flag
gpt有时候会翻译出错误代码,对着字节码阅读下修改写出解密脚本
1 | import base64 |
BadCoffee
0x00 Routine Check Shell
js混淆题
0x01 调试与审计
调试
然而我们可以先调试看看,在与js同目录创建一个index.html,内容为
1 | <script src="./BadCoffee.js" type="text/javascript" charset="utf-8"></script> |
随后在该目录
1 | python3 -m http.server |
即可调试该js,那么代码是经过混淆的,然而有个很直观的enc,直接开调该函数即可
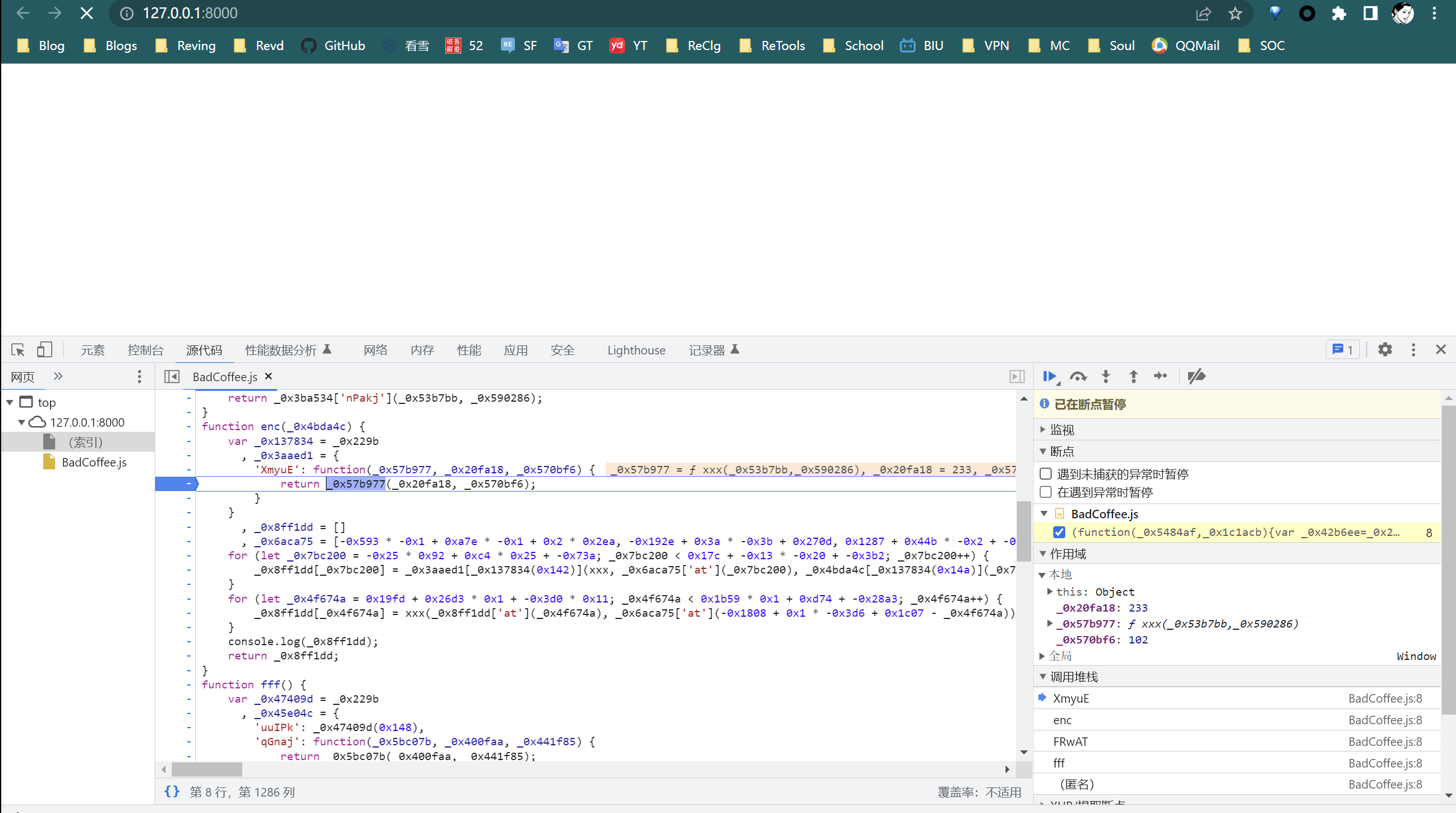
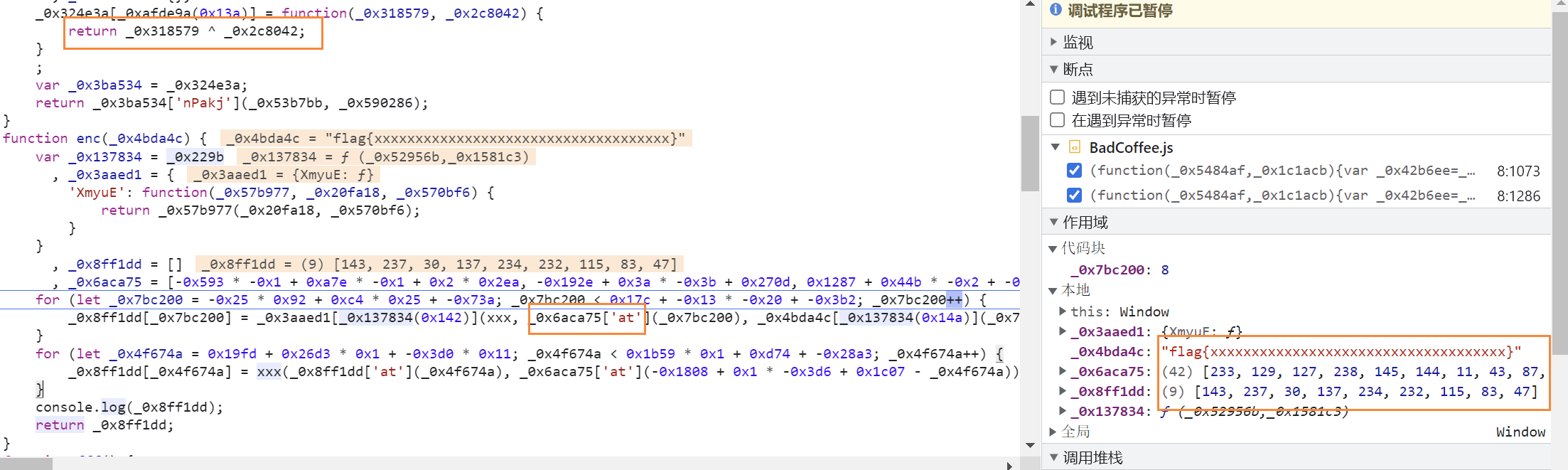
不难发现就是这两个循环在对flag进行加密,稍微调试下再观察堆栈不难发现加密过程
审计
那么当然也可以手动审计下,分析下这两个循环,不难发现就是把这个key从头到尾然后再从尾到头异或了一遍
1 | function enc(input) { |
0x02 Get Flag
那么接着调试拿到密文直接就可以拿到flag了
1 | key = [233, 129, 127, 238, 145, 144, 11, 43, 87, 134, 243, 158, 197, 216, 111, 136, 152, 29, 204, 31, 26, 228, 39, 148, 215, 220, 90, 76, 251, 57, 183, 184, 150, 157, 156, 176, 13, 41, 30, 86, 244, 8] |
Web&Assembly
0x00 Routine Check Shell
wasm题,可以调,但可以先审审看
0x01 JEB & Ghidra
直接运行可以得到以下信息,可以知道梓曰师傅还是给了很多提示的
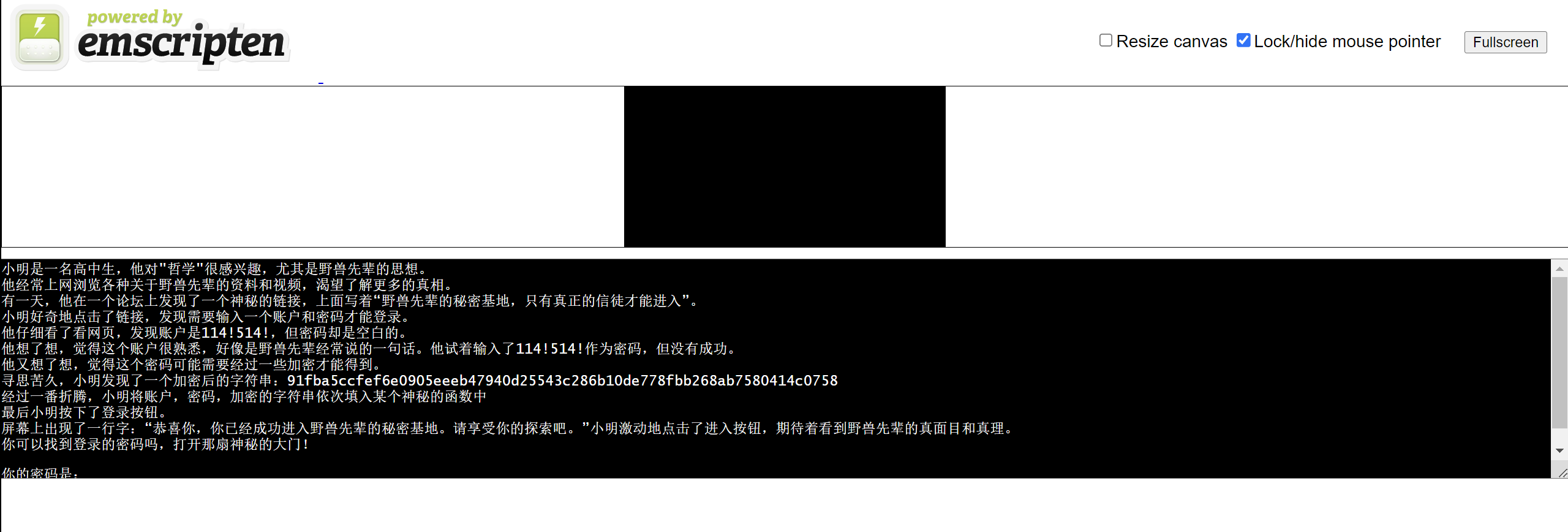
于是我是先拉入JEB审计,看到主函数还是比较好理解的,关键就是F8函数传入的三个值,密钥、输入和密文,当然提示里都告诉你了
1 | int __f9() { |
然而这个F8函数在JEB里就是依托,此时就应该上Ghidra,装一个wasm插件
此时再点入F8函数再稍作审计,就会比较直观
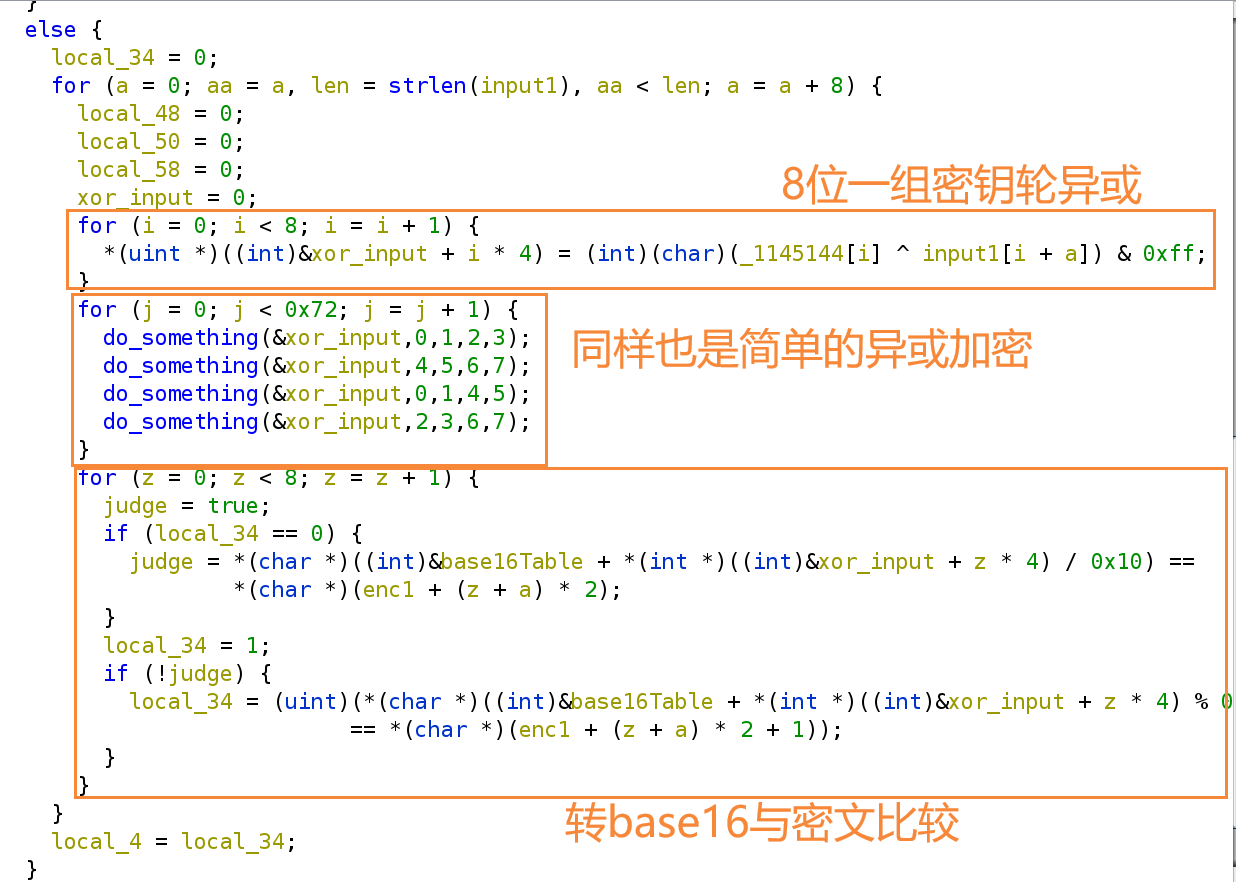
那么加密过程就是
1 | def do_something(input, a, b, c, d): |
0x02 Get Flag
解密直接倒着来着即可
1 | def redo_something(enc, a, b, c, d): |
那么当然此题也可以调试出,不过WASM调试是有一定的冗长得根据堆栈信息配合着静态审计,因为不乏有信息是调试才能得知,可以参考下去年底RCTF的那题WASM题。


About this Post
This post is written by P.Z, licensed under CC BY-NC 4.0.