乘法逆元 + struct库学习!这两个知识点拖了好久,这几天终于把他们学习了一部分
0x00 乘法逆元
事实证明有时候爆破和Z3不好使就得想想这个
言简意赅

1 | 3 * 6 mod 7 = 4 |
(公式块真好玩,到网页直崩呜呜呜)
0x01 struct
终于把这个模块学了,不用跑去DEV调数据的大端小端序了(python真好
文章参考
https://blog.csdn.net/weixin_52640415/article/details/125005006
HI
所以这次其实两道题都是乘模运算,第一题直接Z3秒了,第二题想着爆破都爆不出来就懵了
然后知道了乘模运算怎么逆,于是这两题都采用乘法逆元的方法去解
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
注意的点
- 两此移位直接归0
- v5前的 (_BYTE)
写出等式直接解即可
1 | 23 * input mod 256 + x = c |
EZMATH
把dll拉进dnSPY64(好久没用了
1 | using System; |
程序先经过 乘模加密 再经过 移位加密
那么逆回去就是先 移位解密 再 乘法逆元
EXP
于是写了自己和看了别人的,不同视角解题(慢慢学习struct包
1 | from gmpy2 import invert |
C版EZMATH
1 |
|
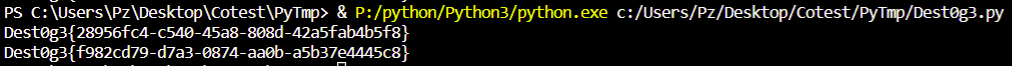
GetFlag!

🍬

🍪
About this Post
This post is written by P.Z, licensed under CC BY-NC 4.0.