0x00 日常查壳
upx,直接脱脱不掉,直接ESP定律脱
(详细可见 UPX壳分析)
0x01 sub_401000
通过调试发现输入的地方在401000函数
逻辑还是挺乱的,不过慢慢调试是关键几个函数在干什么(我不理解这是经过什么混淆?)
1 | int sub_401000() |
因为看到后面有base64加密的痕迹,所以大概是判断这几个函数里有base64加密,但不是标准加密,是变表
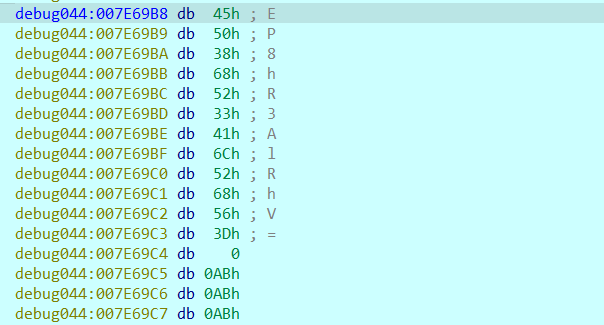
sub_401233
只能说里面乱的不得了,通过到处找,发现这里可以找到码表
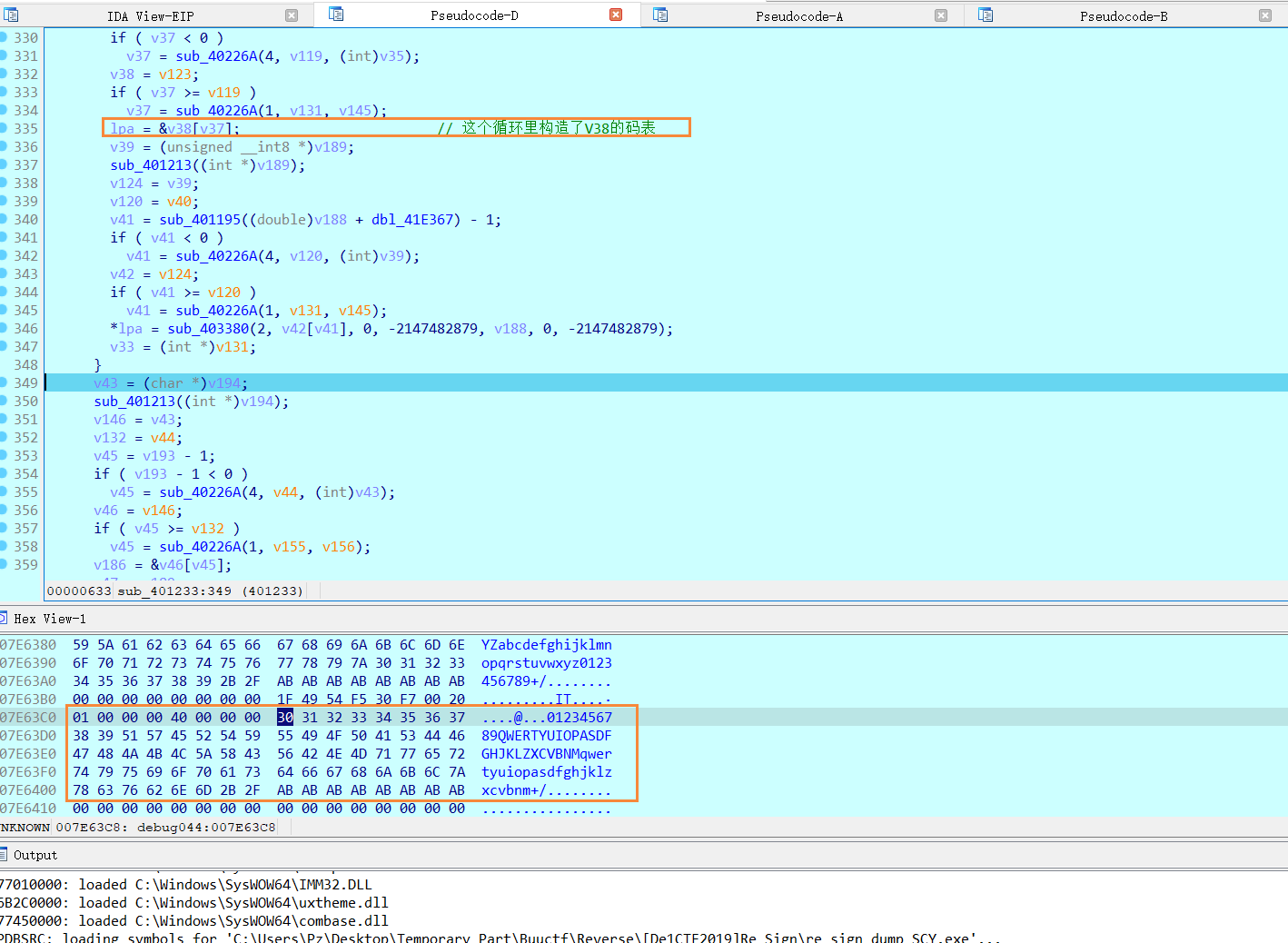
0x02 sub_401F0A
这里是判断flag的地方,大略阅读可以得知长度为48
比较关键是的这里,v33是我们加密后的base64,v19是密文

FindIndex
第一次传入的是‘E’,每次都会压入正常的base64码表
1 | UPX0:00402190 loc_402190: ; CODE XREF: FindIndex+29↑j |
通过多次调试可以发现,会返回数组下标 + 1
就比如第一个字符是E,返回的是5
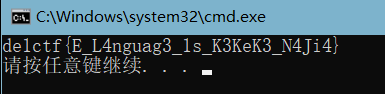
0x03 GetFlag!
返回之后再和v19对比,我们把v19里的数组拿出,直接逆即可
- 拿base64表下标减1恢复,经过变表加密的flag
- 拿变表解密字符串
- GetFlag!
1 |
|
GetFlag!

🍬

🍪
About this Post
This post is written by P.Z, licensed under CC BY-NC 4.0.