上次做这个架构的题还在上次,ZJ省赛的unicorn记忆尤新
0x00 日常查壳
虽然是.bin后缀但其实就是arm文件,binwalk跑不出来啥
可以学习下这篇文章如何应对arm文件逆向
https://bbs.pediy.com/thread-249844.htm
0x01 准备分析ARM
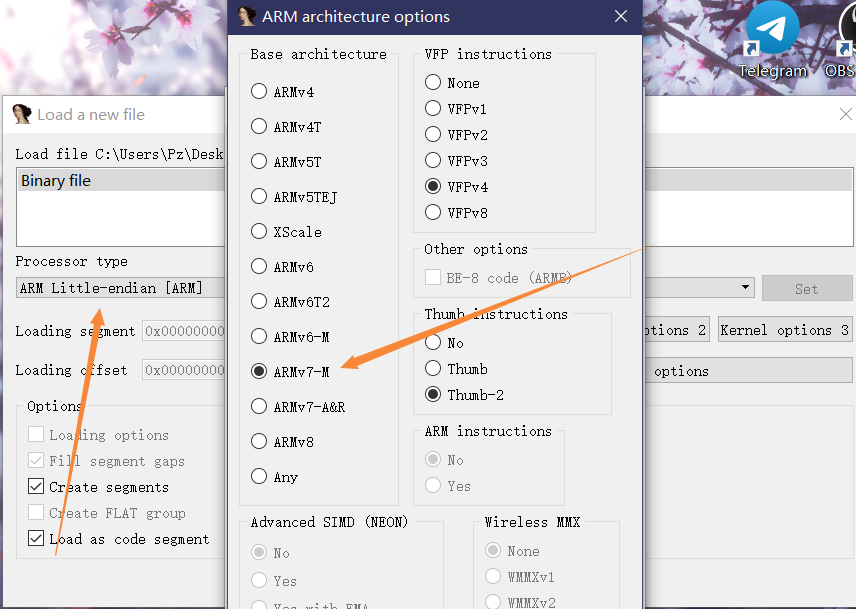
首先要选好架构,这个v7-M还是看了wp才知道,不过我有点好奇怎么才能分辨是v几,因为不选的话进去没法分析
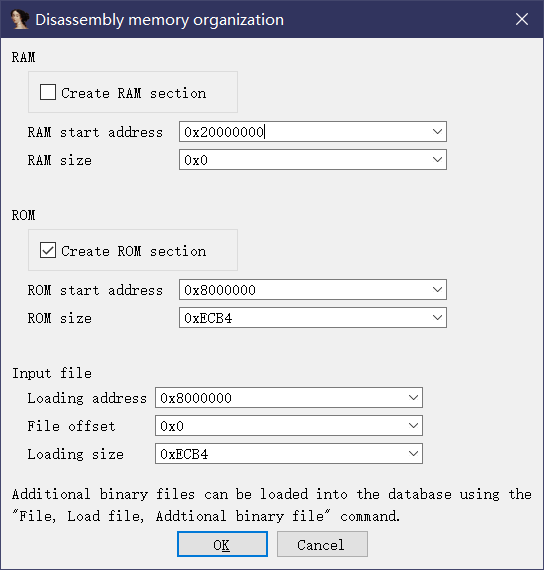
再进去可以看到让填基地址,不过先进去才能知道填什么,直接确定
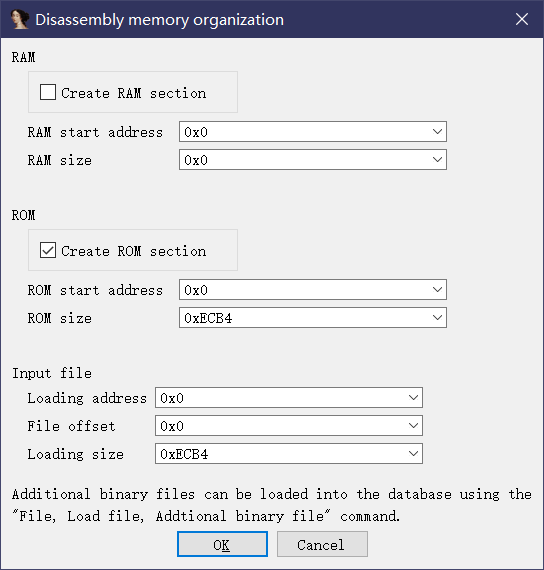
由这里可以知道RAM和ROM的基地址,详情见放文头的那篇文章
1 | ROM:00000000 DCD 0x20010000 //RAM 0x20000000 |
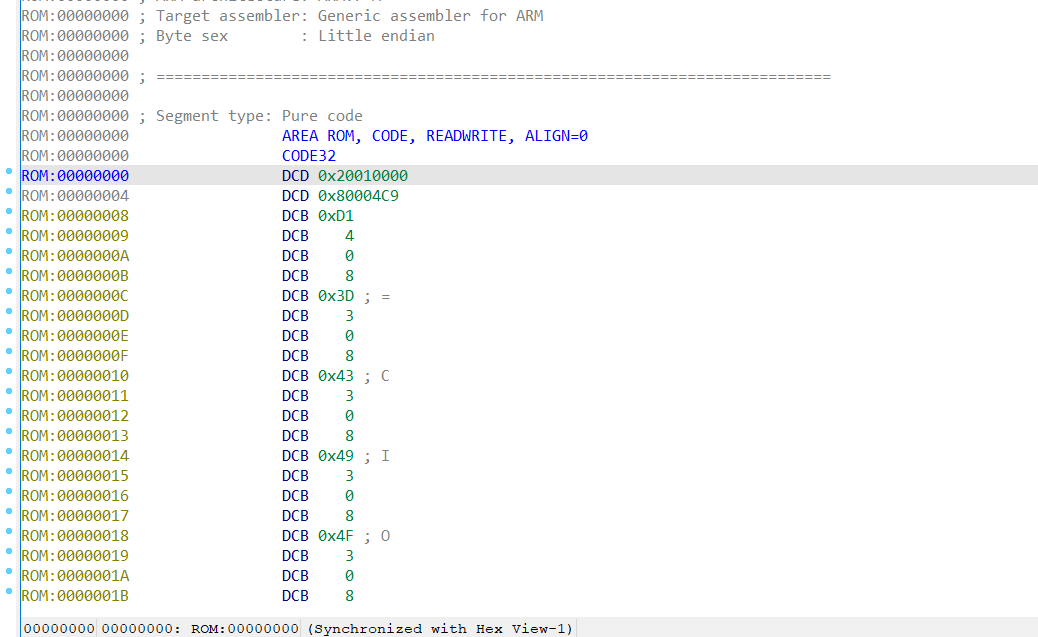
第一个是RAM填入,第二个ROM填入,第三个应该是文件加载地址
进去直接按C再P就全部恢复了,通过查找main字符串到这
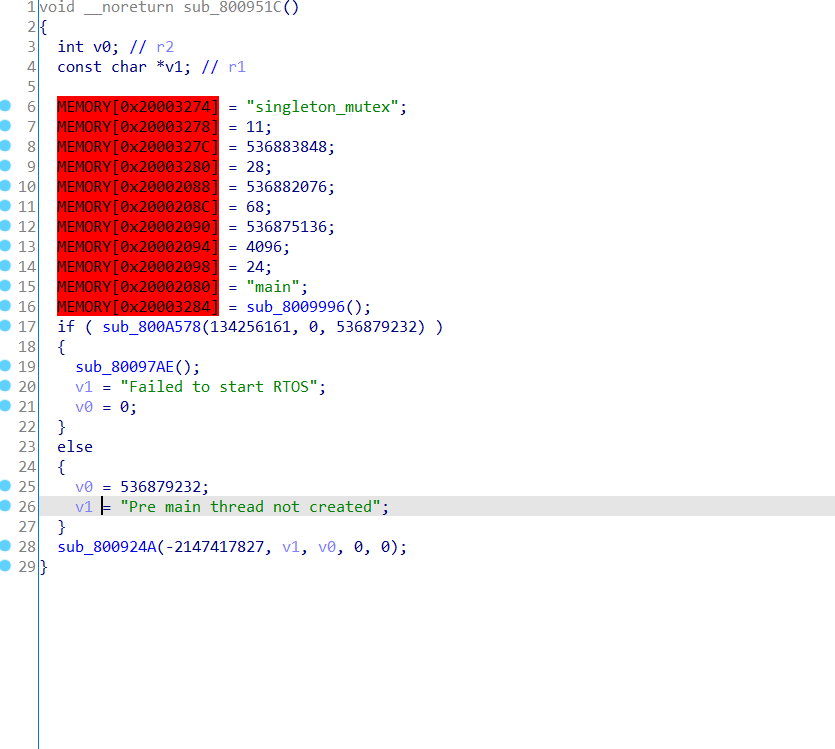
发现有段还没定义,于是手动创建这个段
关于地址的开始和结束可以自己去文件里逛逛,命名随意
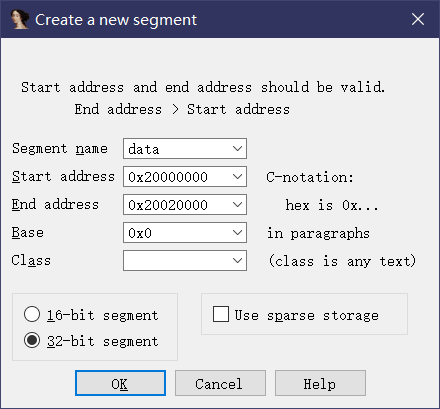
创完再去赋个权限,ctrl + s调出
alt + s全部拉满
0x02 MAIN函数
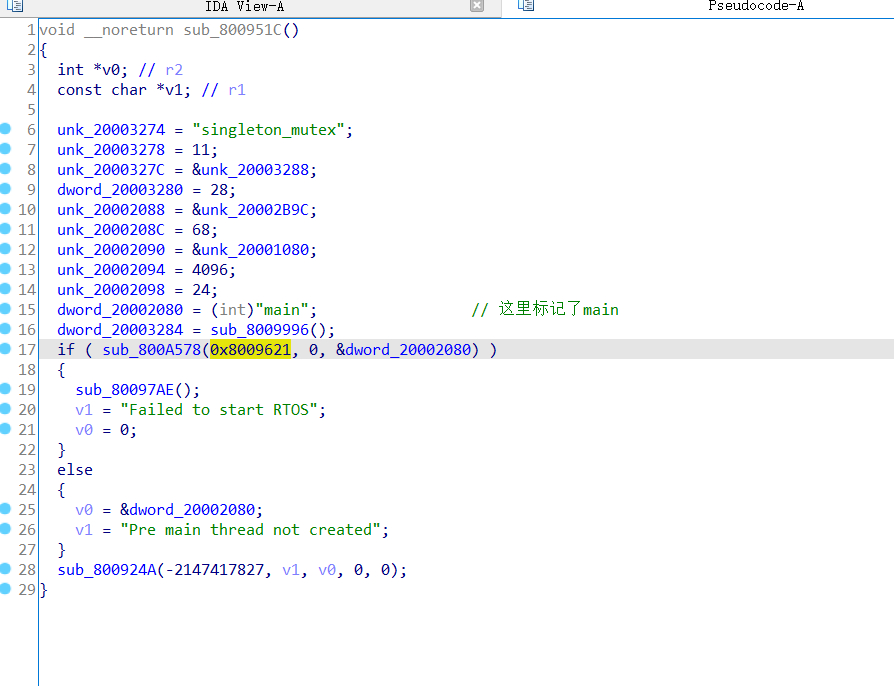
再回到main函数,按u按c再p,全部恢复
由于历史遗留还什么问题,8009621的其实是8009620,这里放到了800A578来调用
手动去8009620
继续往里找
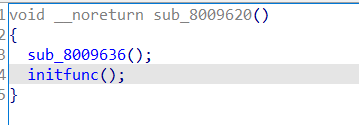
F5有点没法恢复,直接看汇编即可,分别去分析每个调用
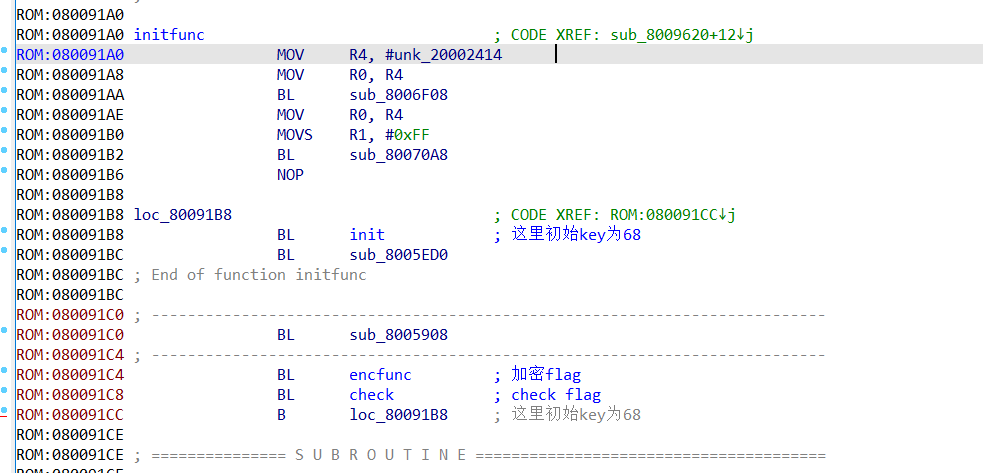
init
这里主要是index和key的初始化
1 | char *init() |
check
看encfunc前可以先看check,这边是可以猜出通过交叉引用找到那个encfunc,不管是从Index还是flag
1 | int check() |
encfunc
这边的主要还是xorflag和changekey,其他对index和key或是flag都没有变化就不需要关注
1 | int encfunc() |
xorkey
从这里可以拿到密文
1 | int xorflag() |
changekey
注意一下v1 v2和key三行语句即可,每次这里调用完又回到xorkey
PS:先执行了一遍xorflag再来到了这changeflag,然后再回去xorkey
1 | _DWORD *changekey() |
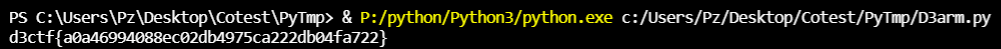
0x03 GetFlag!
于是分析完执行流程,再去写脚本就比较容易了
1 | enflag = [ |
GetFlag!


About this Post
This post is written by P.Z, licensed under CC BY-NC 4.0.