哈哈,搭环境,有趣有趣
(关于搭了一天环境搞烂一台虚拟机又重装一遍坚持不懈装完一个强迫症快照归0)
难受入睡 无力起床 鼓起勇气 回到机房 熟悉报错 瞬间解决
0x00 日常查壳
python虚拟机题,出题人自己弄了个so文件,于是要去linux下弄个python3.10
1 | import byte_analizer as ba |
0x01 分析opcodes
用好用的ipython反复调试可以发现
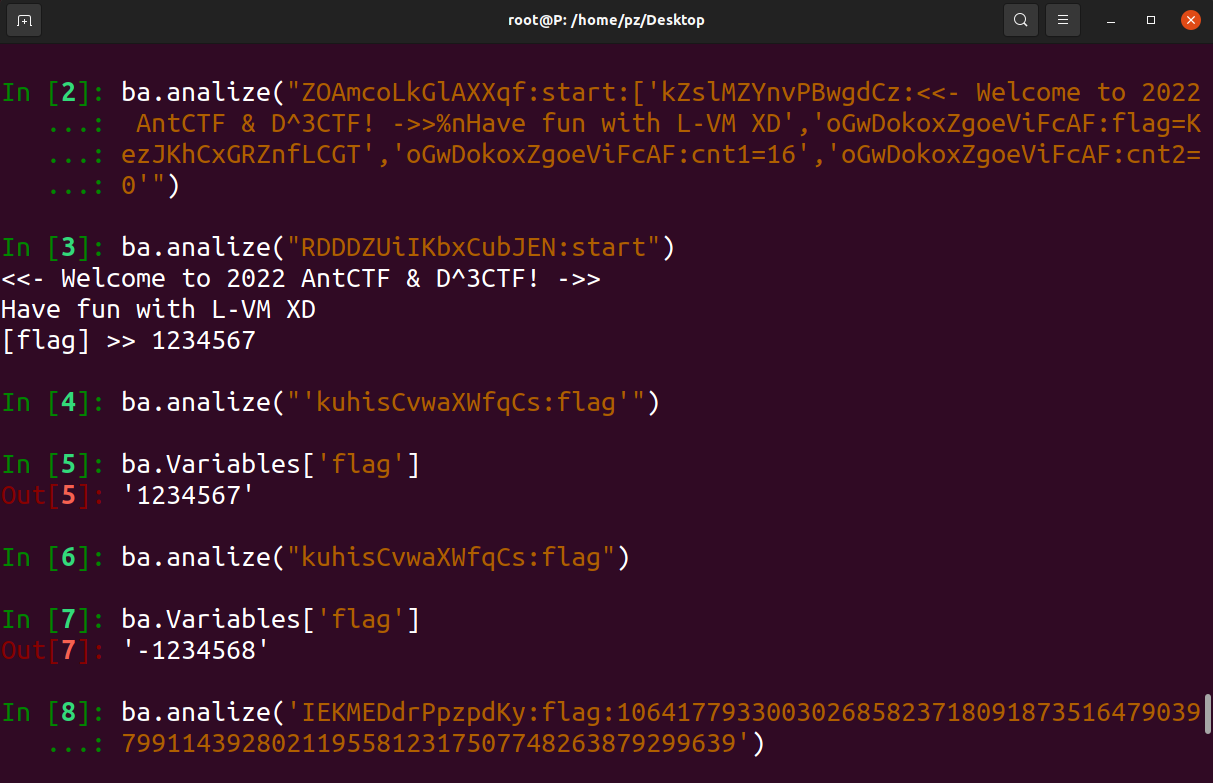
1 | ZOAmcoLkGlAXXqf:xxx // 定义函数xxx |
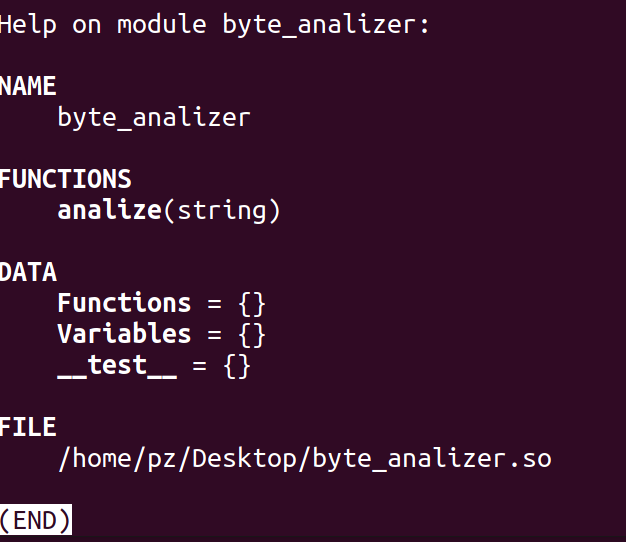
help(ba)可以查看这个库的说明文件
再看结尾的几个执行操作,所以我们只要关心okokokok函数怎么执行的
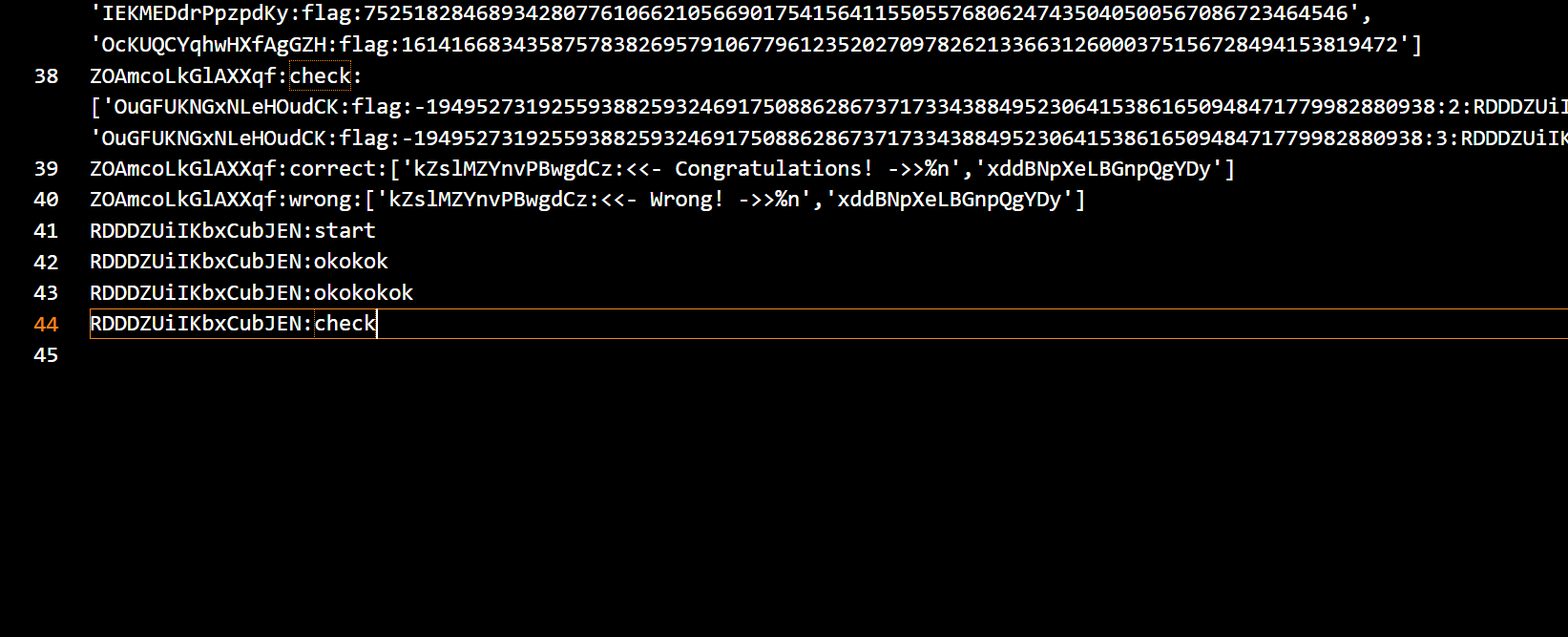
0x02 GetFlag!
把okokokok函数的内容单独拿出来
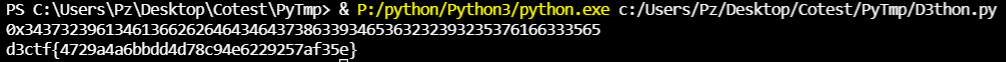
上脚本
1 | # IEKMEDdrPpzpdKy + |
GetFlag!

🍬

🍪
About this Post
This post is written by P.Z, licensed under CC BY-NC 4.0.