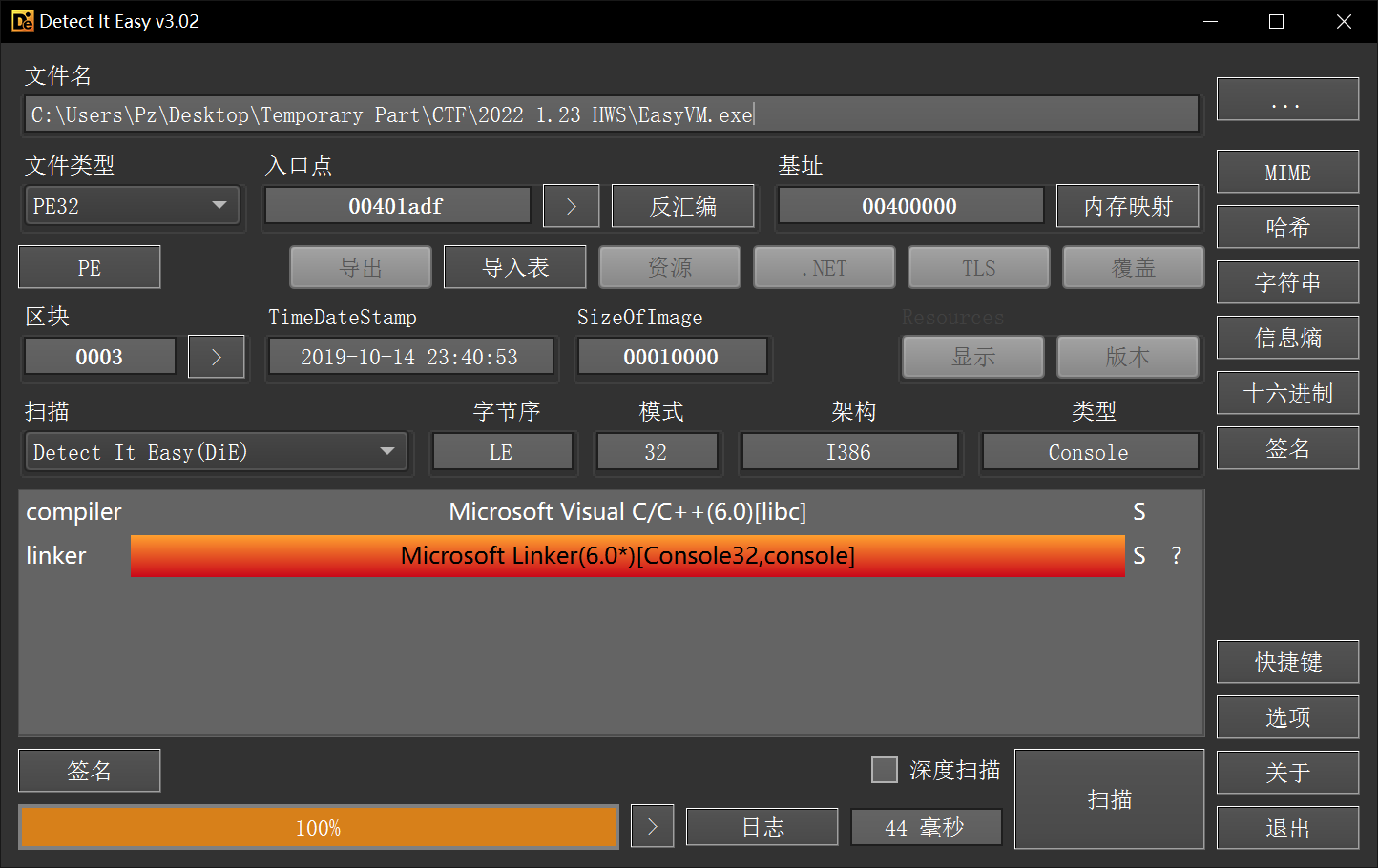
0x00 日常查壳
无壳32位
0x01 分析主函数
通过shitf+F12找到字符串,交叉引用到这,这边有几个常见的花指令jz jnz这种的
可以参考之前我录的一期:绿城杯-Reverse(逆向)-babyvxworks 浅谈花指令_bilibili
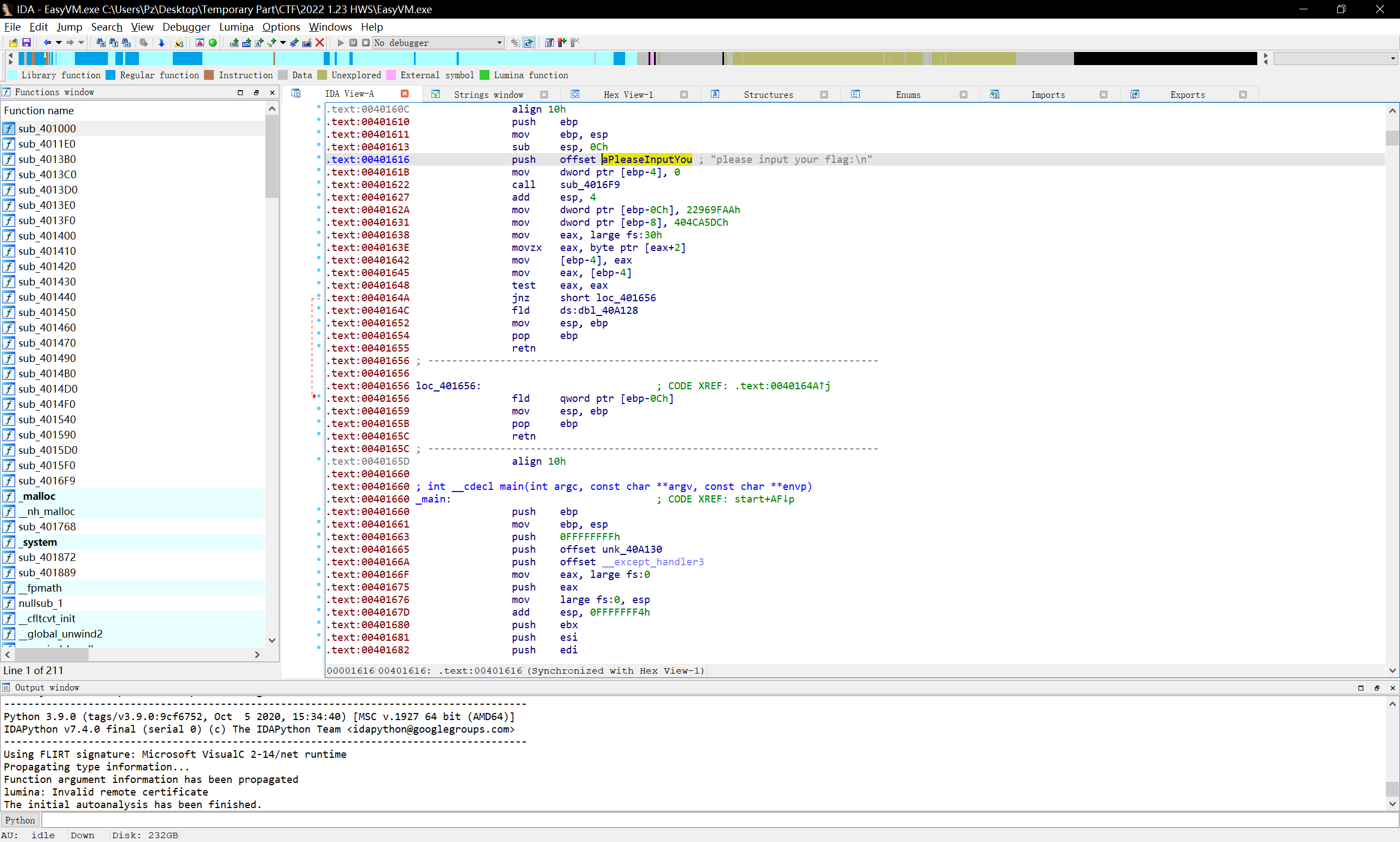
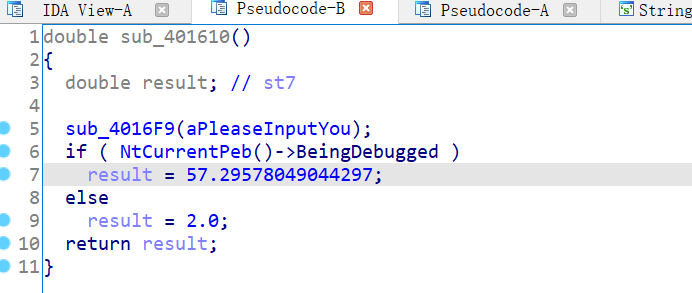
反汇编出来的ida看不出来什么东西,ida动调不起来,老是闪退,于是就去dbg去做这题
去翻函数列表可以发现4012F0是关键区域,在main函数里一步步跟会找到跳到那的位置
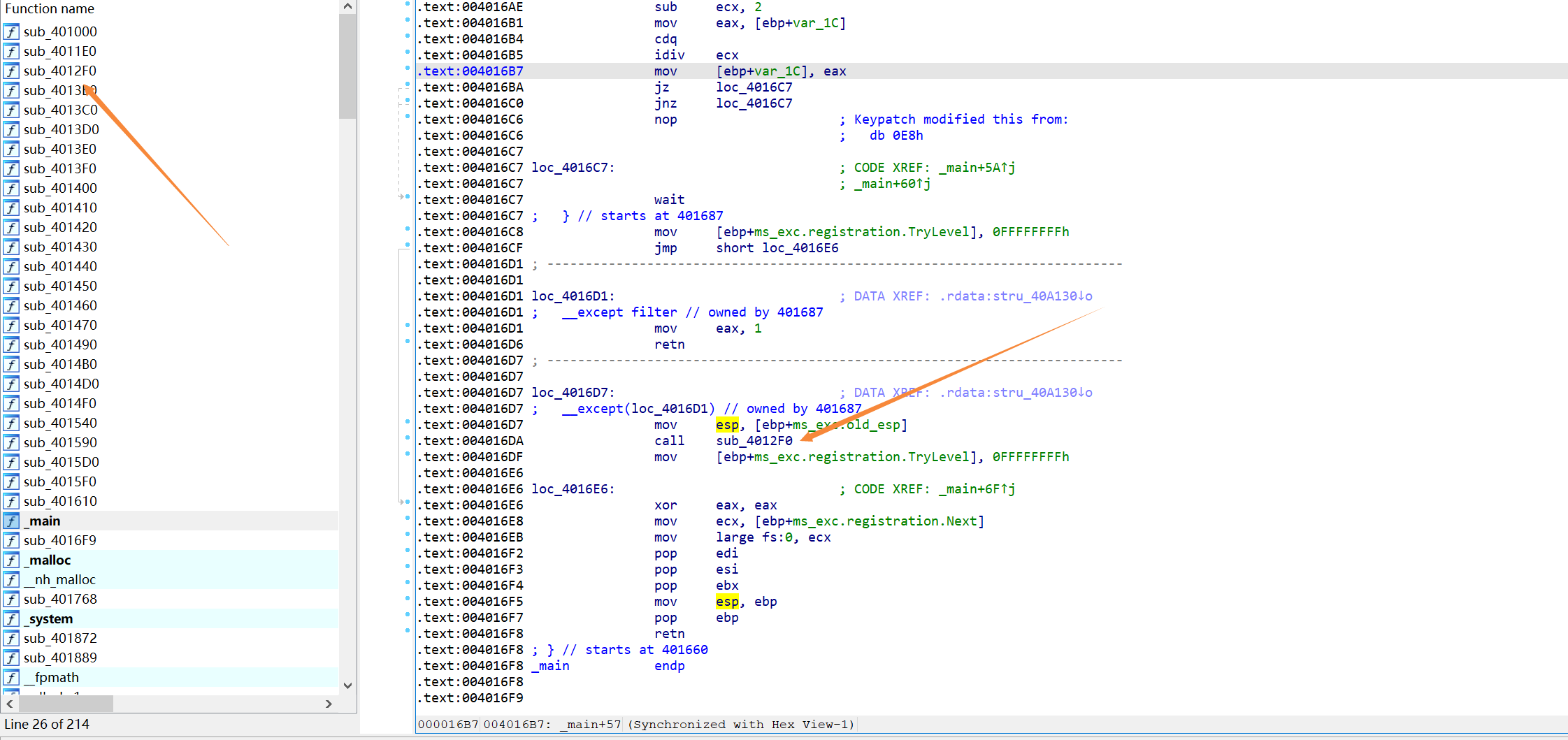
0x02 分析4012F0
VM的题就是操作数和操作码,确定了符号执行的函数,慢慢跟就好了
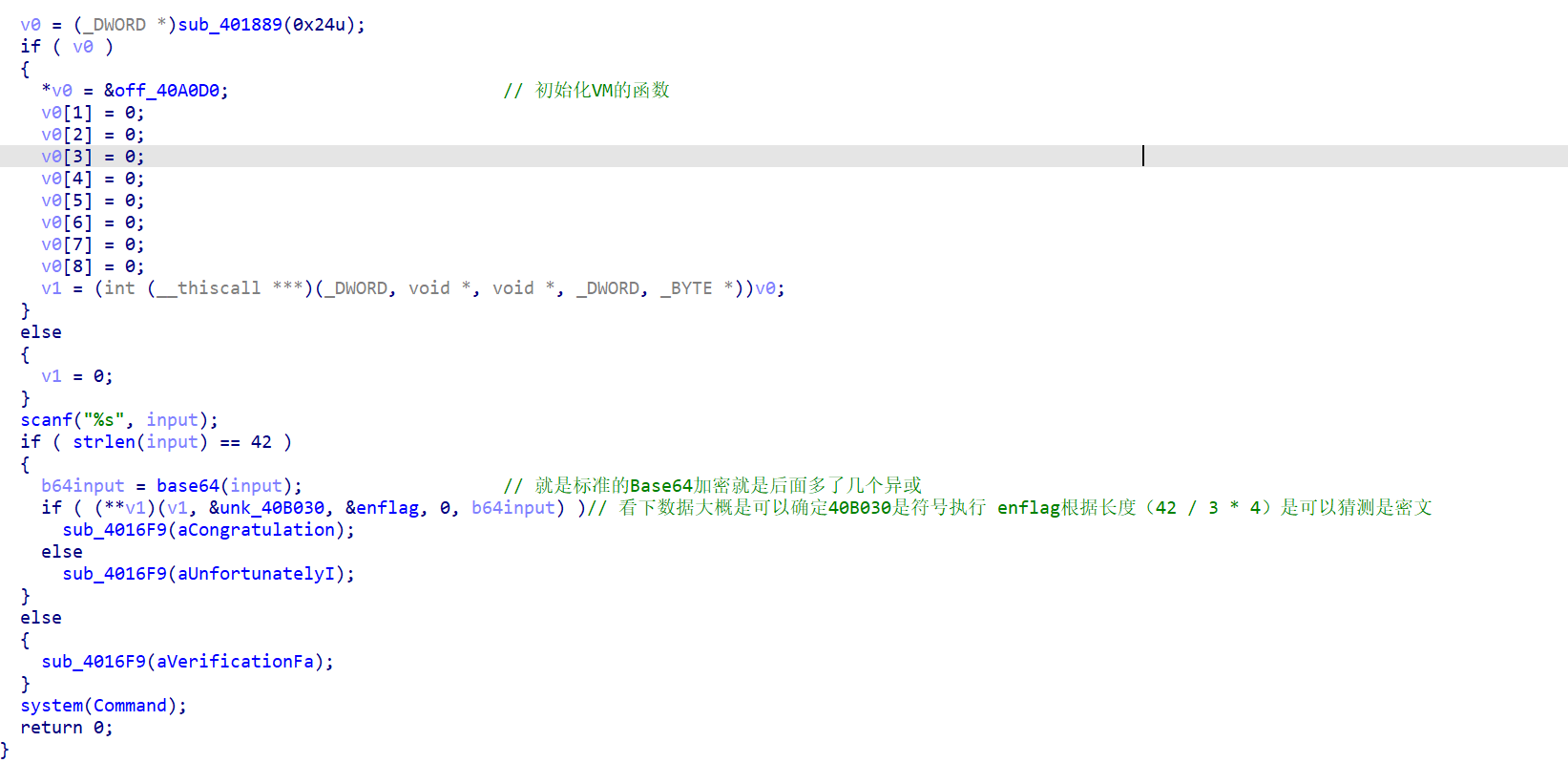
关键就注意这三块数据即可,现在只要搞清楚每个符号执行是干嘛就可以了
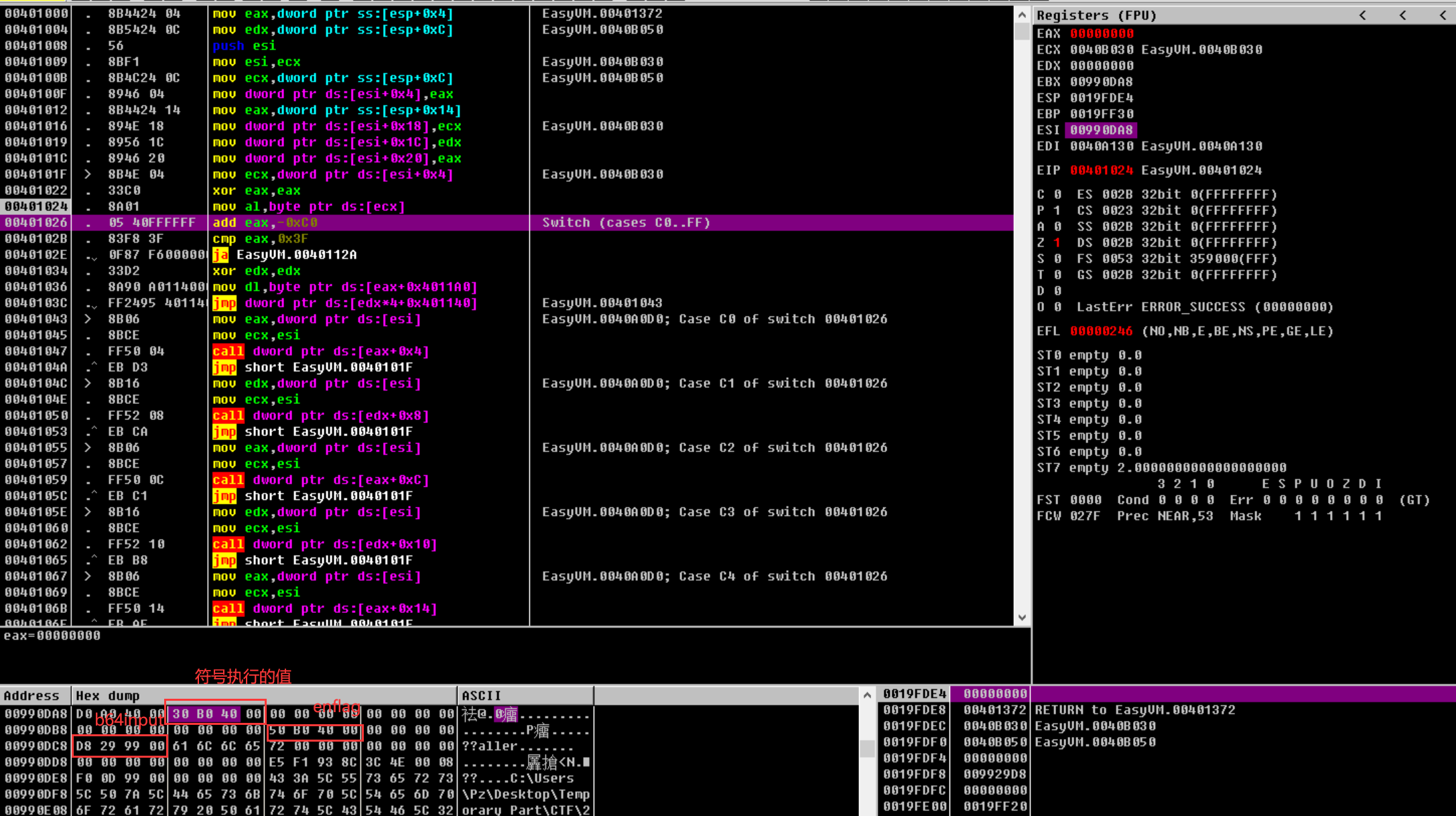
一条语句跟着看数据得到分析
于是可以得到一个等式:
当i = 0: flag[i] = eflag[i] ^ 0xEE
当i > 0: flag[i] = eflag[i] ^ eflag[i - 1] ^ 0xEE
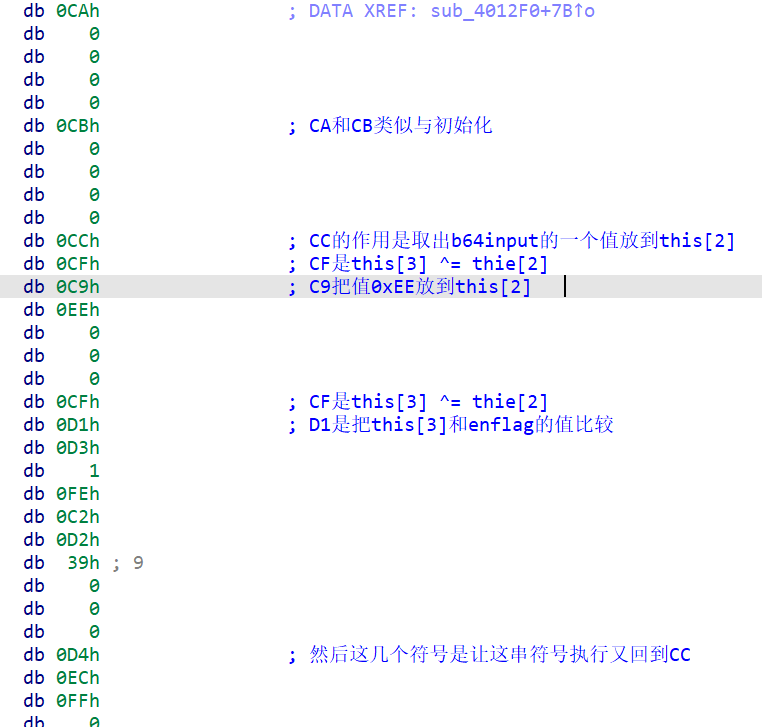
0x03 GetFlag!
于是我们恢复一下enflag这串数据,顺便把base64后的几个异或解决
1 |
|
拿到数据后,base64标准解密即可
1 |
|
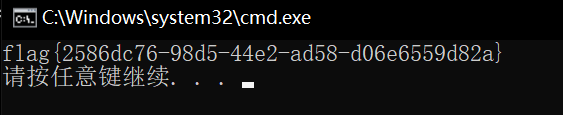
GetFlag!

🍬

🍪
About this Post
This post is written by P.Z, licensed under CC BY-NC 4.0.